In a broader sense, any kind of manipulation linked to behavioral psychology can be considered social engineering. However, the concept is not always related to criminal or fraudulent activities. In fact, social engineering is being widely used and studied in a variety of contexts, in fields like social sciences, psychology, and marketing.
When it comes to cybersecurity, social engineering is performed with ulterior motives and refers to a set of malicious activities that attempt to manipulate people into making bad moves, such as giving up personal or confidential information that can be later used against them or their company. Identity fraud is a common consequence of these types of attacks and in many cases leads to significant financial losses.
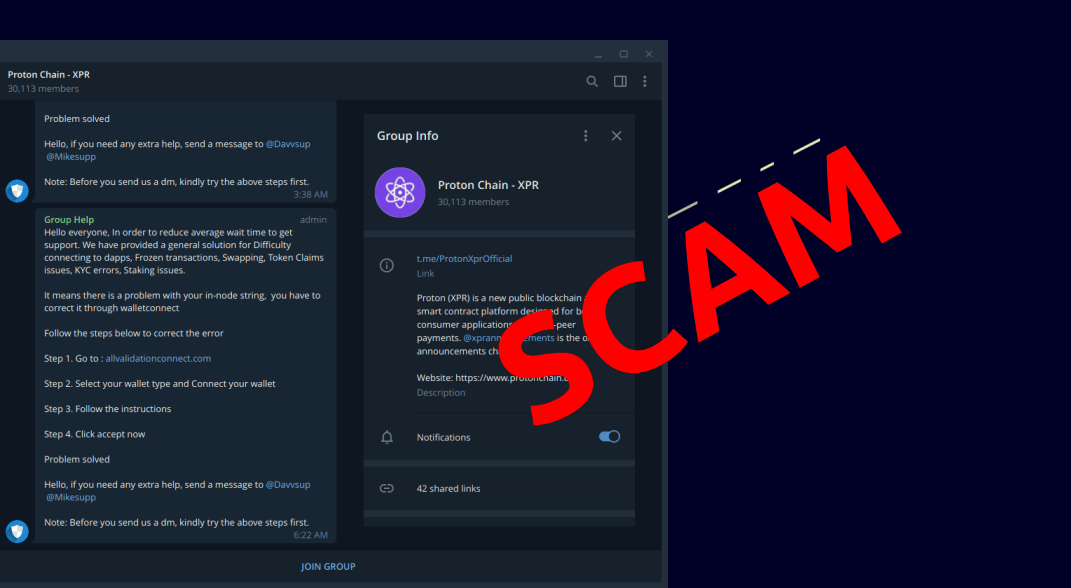
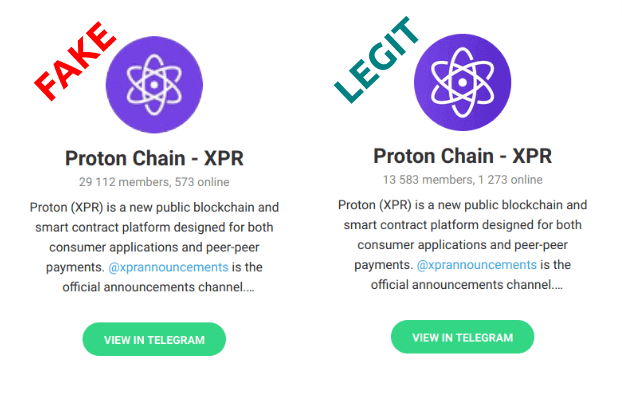
Social engineering is often presented as a cyber threat, but the concept exists for a long time, and the term may also be used in relation to real-world fraudulent schemes, which usually involve impersonation of authorities or IT specialists. However, the emergence of the internet made it much easier for hackers to perform manipulative attacks on a wider scale and, unfortunately, these malicious activities are also taking place in the context of cryptocurrencies.
How does it work?
All types of social engineering techniques rely on the weaknesses of human psychology. Scammers take advantage of emotions to manipulate and trick their victims. People’s fear, greed, curiosity, and even their willingness to help others are turned against them through a variety of methods. Among the multiple sorts of malicious social engineering, phishing is certainly one of the most common and well-known examples.
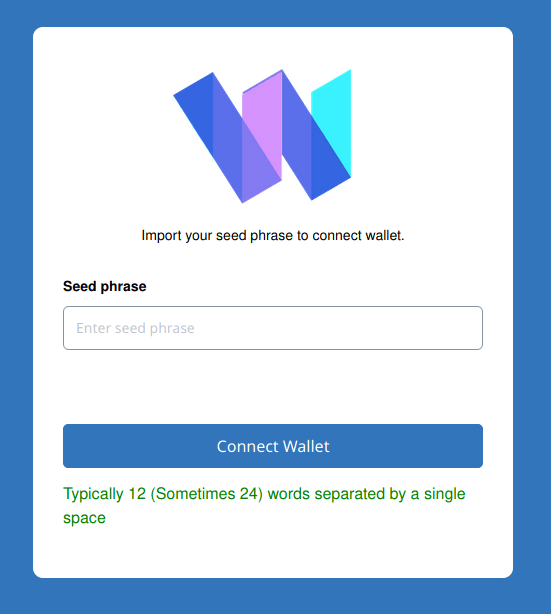
Phishing
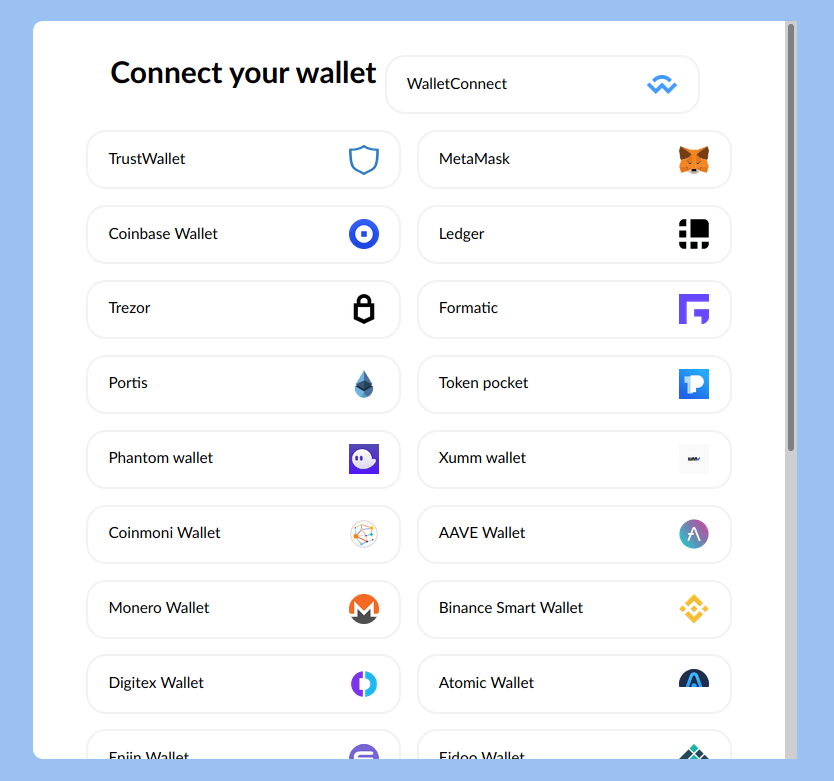
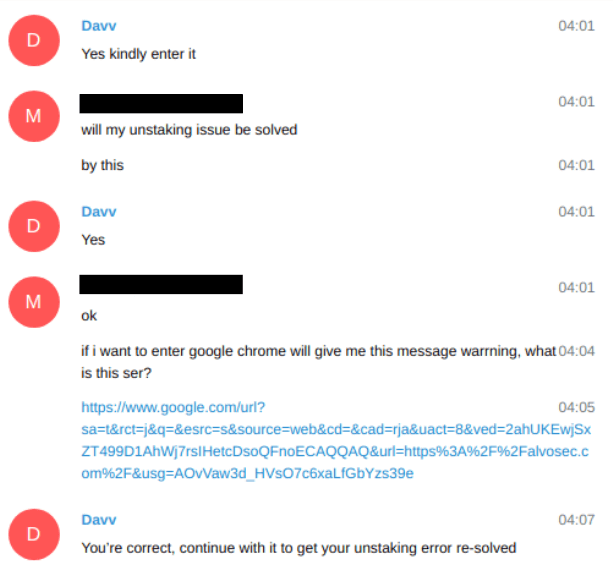
Phishing emails often mimic correspondence from a legitimate company, such as a national bank chain, a reputable online store, or an email provider. In some cases, these clone emails will warn users that their account either needs to be updated or has shown unusual activity, requiring them to provide personal information as a way to confirm their identity and regularize their accounts. Out of fear, some people promptly click the links and navigate to a fake website in order to provide the required data. At this point, the information will be in the hands of the hackers.
Scareware
Social engineering techniques are also applied to spread the so-called Scareware. As the name suggests, scareware is a type of malware designed to scare and shock users. They typically involve the creation of false alarms that attempt to trick victims into installing a fraudulent software that looks legitimate, or into accessing a website that infects their system. Such a technique often relies on users’ fear of having their system compromised, convincing them to click on a web banner or popup. The messages usually say something like: “Your system is infected, click here to clean it.”
Baiting
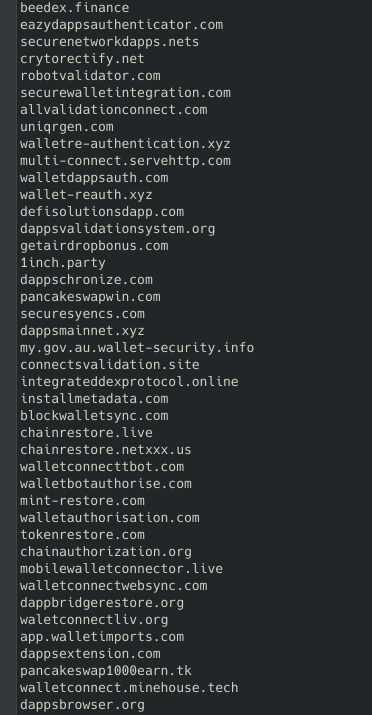
Baiting is another social engineering method that causes trouble for many inattentive users. It involves the use of baits to lure victims based on their greed or curiosity. For instance, scammers may create a website that offers something for free, like music files, videos, or books. But in order to access these files, users are required to create an account, providing their personal information. In some cases, there is no need for an account because the files are directly infected with malware that will penetrate the victim’s computer system and collect their sensitive data.
Baiting schemes may also occur in the real world through the use of USB sticks and external hard drives. Scammers may intentionally leave infected devices on a public place, so any curious person that grabs it to check the content ends up infecting their personal computer.
Social engineering and cryptocurrencies
A greedy mentality can be quite dangerous when it comes to financial markets, making traders and investors particularly vulnerable to phishing attacks, Ponzi or pyramid schemes, and other types of scams. Within the blockchain industry, the excitement that cryptocurrencies generate attracts many newcomers to the space in a relatively short period of time (especially during bull markets).
Even though many people do not fully understand how cryptocurrency works, they often hear about the potential of these markets to generate profits and end up investing without doing appropriate research. Social engineering is particularly concerning for the rookies as they are frequently trapped by their own greed or fear.
On the one hand, the eager to make quick profits and earn easy money eventually leads newcomers to chase false promises of giveaways and airdrops. On the other hand, the fear of having their private files compromised may drive users to pay a ransom. In some cases, there is no real ransomware infection, and users are tricked by a false alarm or message created by hackers.
How to prevent social engineering attacks
As mentioned, social engineering scams work because they appeal to human nature. They usually use fear as a motivator, urging people to act immediately in order to protect themselves (or their system) from an unreal threat. The attacks also rely on human greed, luring victims into various types of investment scams. So it is important to keep in mind that if an offer looks too good to be true, it probably is.
Although some scammers are sophisticated, other attackers make noticeable mistakes. Some phishing emails, and even scareware banners, often contain syntax mistakes or misspelled words and are only effective against those who don’t pay enough attention to grammar and spelling – so keep your eyes open.
In order to avoid becoming a victim of social engineering attacks, you should consider the following security measures:
- Educate yourself, family and friends. Teach them about the common cases of malicious social engineering and inform them about the main general security principles.
- Be cautious with email attachments and links. Avoid clicking on ads and websites of unknown source;
- Install a trustworthy antivirus and keep your software applications and operating system up to date;
- Make use of multifactor authentication solutions whenever you can to protect your email credentials and other personal data.
- For businesses: consider preparing your employees to identify and prevent phishing attacks and social engineering schemes.
Closing thoughts
Cybercriminals are constantly looking for new methods to deceive users, aiming to steal their funds and sensitive information, so it is very important to educate yourself and the ones around you. The internet provides a haven for these types of scams, and they are particularly frequent in the cryptocurrency space. Be cautious and stay alert to avoid falling for social engineering traps.
Furthermore, anyone that decides to trade or invest in cryptocurrency should do prior research and make sure to have a good understanding of both the markets and the working mechanisms of blockchain technology.
Source