A vulnerability has been discovered in Microsoft Support Diagnostic Tool (MSDT) which could allow for arbitrary code execution. MSDT can be called using the URL protocol from a calling application like Word allowing an attacker to run arbitrary code with the privileges of the user that executed the program. An attacker can entice a victim to open a malicious Word document resulting in code execution without macros enabled. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user's rights.
The attack pattern would be as follows:
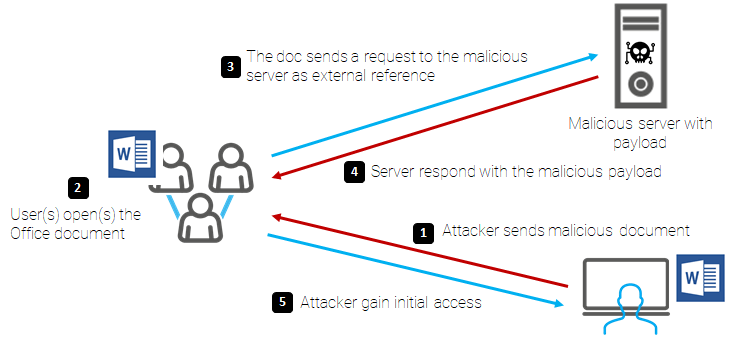
This vulnerability affects systems 7, 10 and 11, Server 2008 to 2022 both 32-bit and 64-bit, regardless of the system language.
To disable the MSDT URL Protocol
Disabling MSDT URL protocol prevents troubleshooters being launched as links including links throughout the operating system. Troubleshooters can still be accessed using the Get Help application and in system settings as other or additional troubleshooters. Follow these steps to disable:
How to undo the workaround
Yara rule to detect
rule Follina_CVE_2022_30190
{
meta:
author = "Joe Security"
reference = "https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e"
strings:
$msdt1 = "ms-msdt:/id" ascii wide nocase
$msdt2 = "ms-msdt:-id" ascii wide nocase
$para1 = "IT_RebrowseForFile" ascii wide nocase
condition:
(1 of ($msdt) and 1 of ($para))
}
References:
CVE
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-30190
Microsoft
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30190
https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
PCmag
https://www.pcmag.com/news/researchers-reveal-follina-zero-day-vulnerability-in-microsoft-office