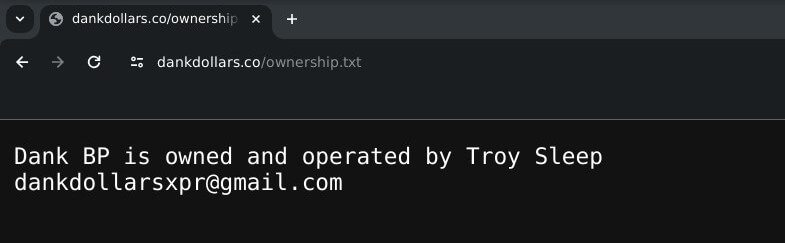
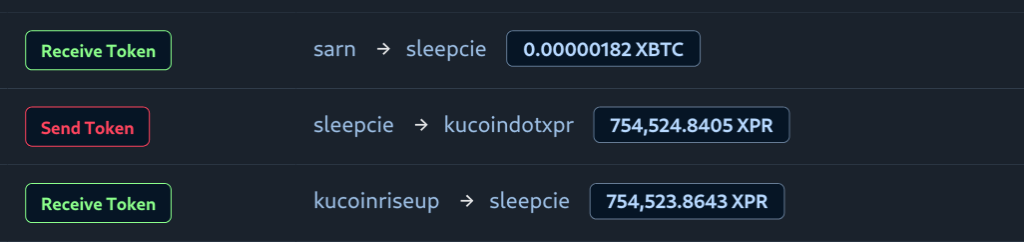
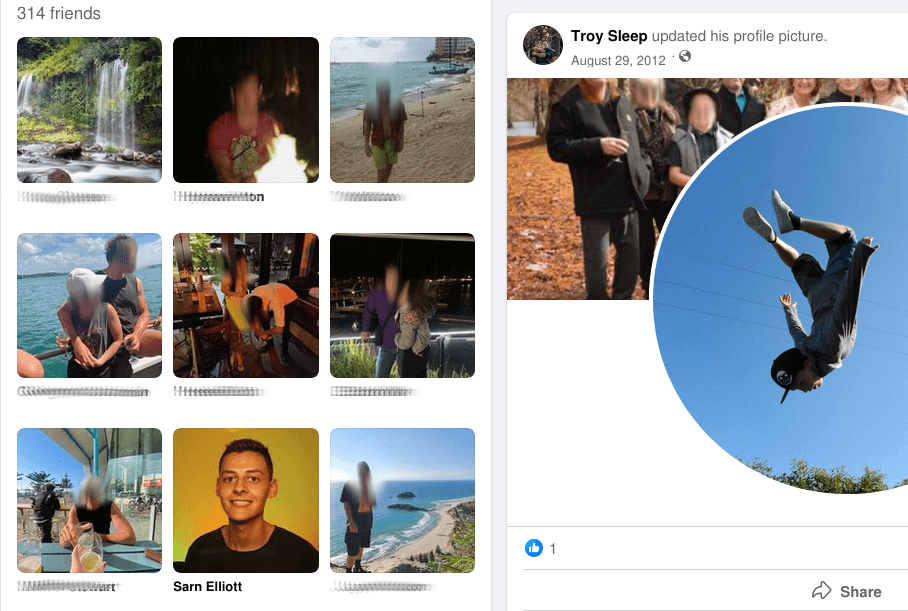
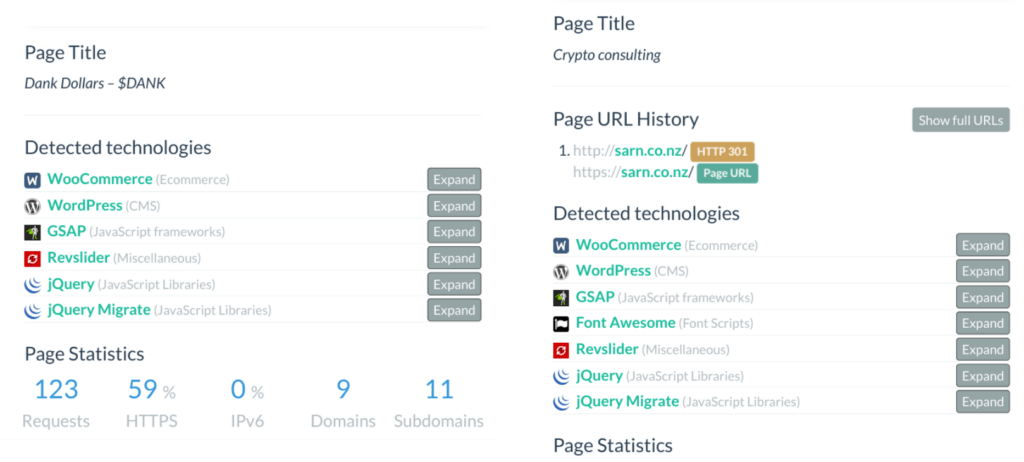
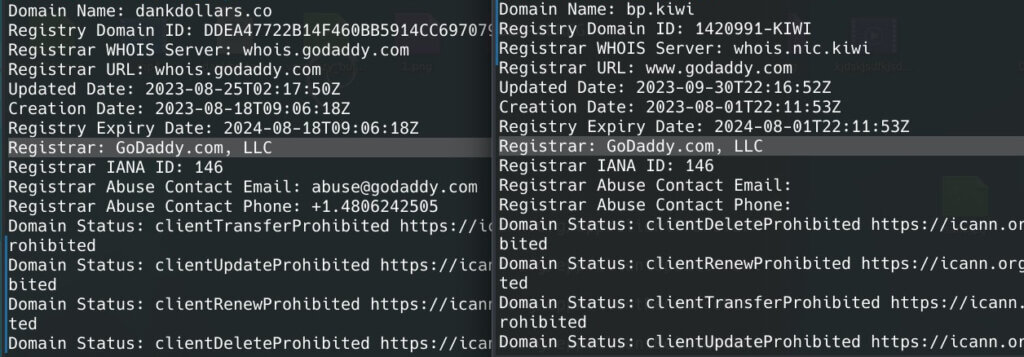
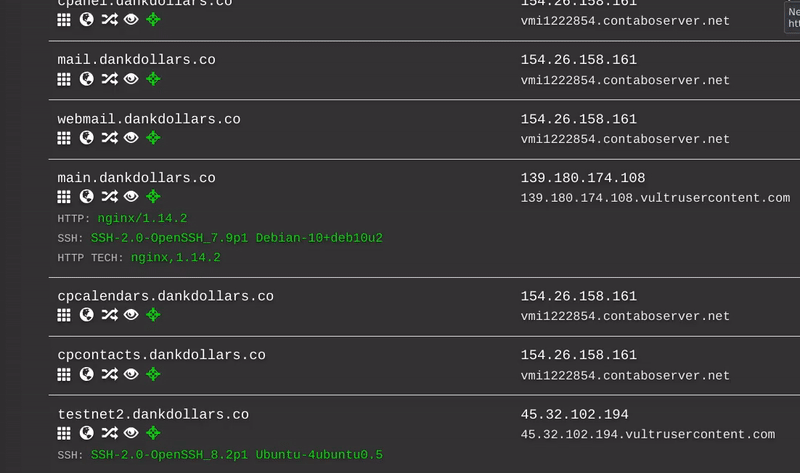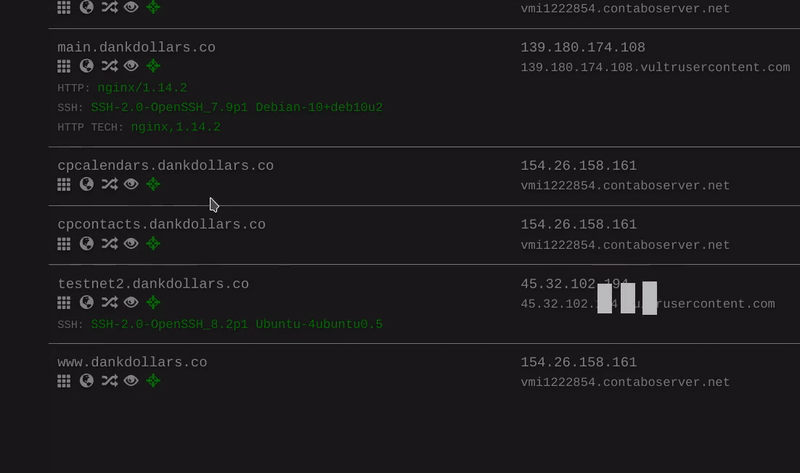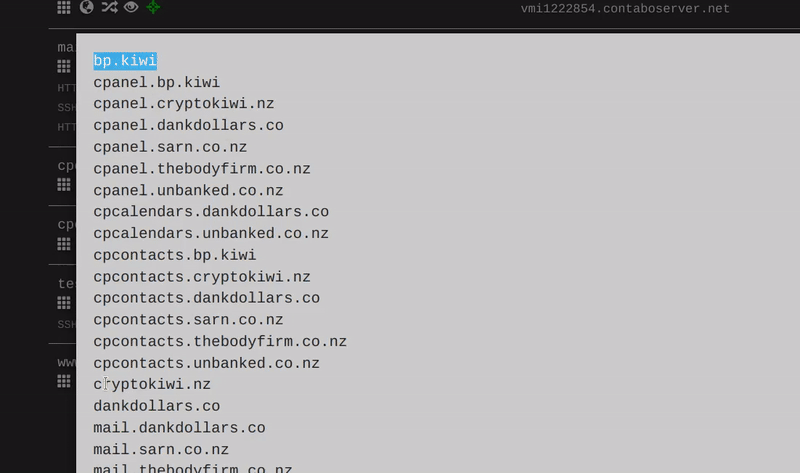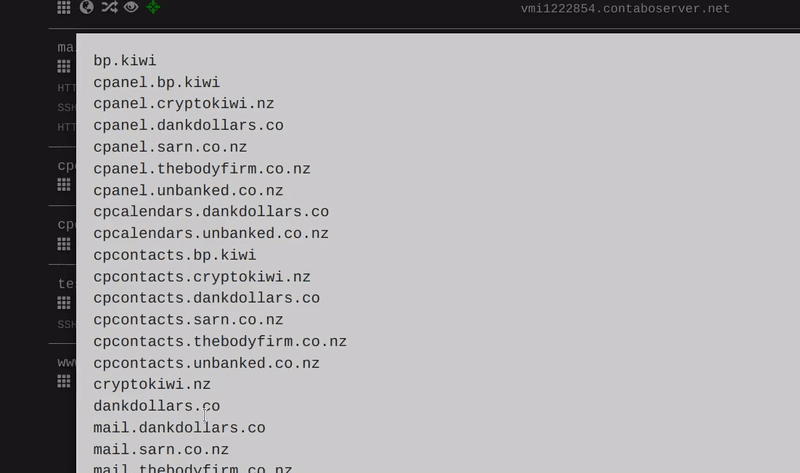
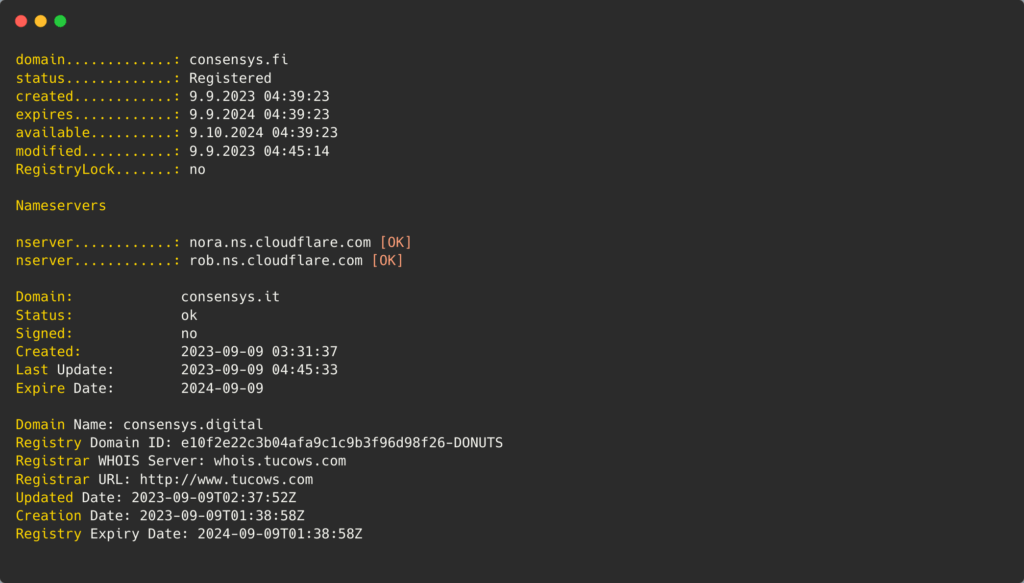
This is a follow-up to our initial research, uncovering that ProtonKiwi was operating two BPs, which goes strictly against XPR Network rules. ProtonKiwi’s decision to engage in more lies and deception is a significant misstep, moving away from a constructive solution. In this article we will reveal even more lies from this ex-BP.
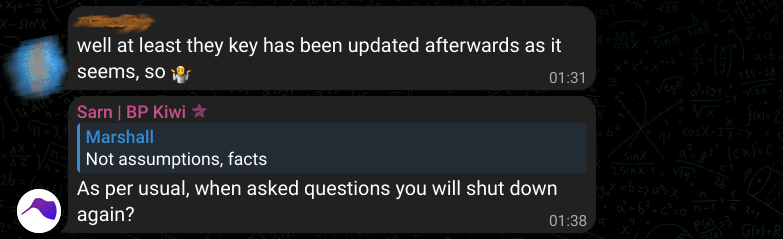
Someone from users brought up in the chat that keys were later updated. The valid concern raised deserves a detailed response.
Let’s make a chronology of DankBP’s keys:
October 2, 2023 – From the video it’s evident that he had access to DankBP’s private keys since October 2, 2023.
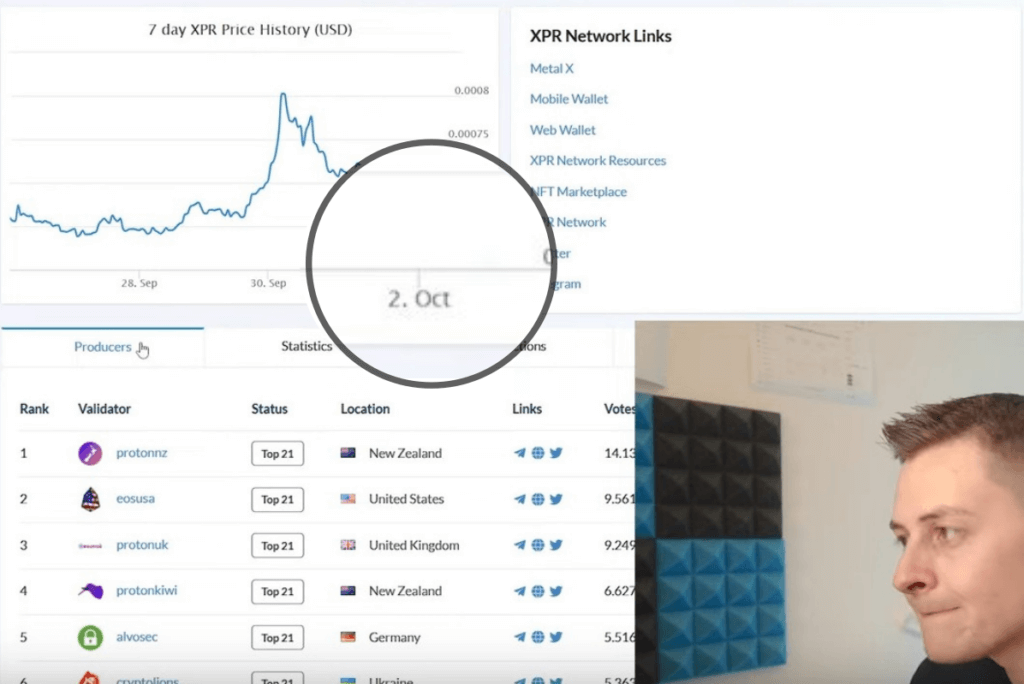
October 7, 2023 – Sarn uploaded video to his channel titled “Telos Proposal: Telos Voting Reform”, where he is logged into DankBP wallet.
Update
The DankDollar Telegram group and the YouTube video from ProtonKiwi are now private, while the website is in “maintenance mode.”
Video Clip with the Title: “Telos Proposal: Telos Voting Reform”
October 16, 2023 – He created producer key and registered with that key on mainnet.
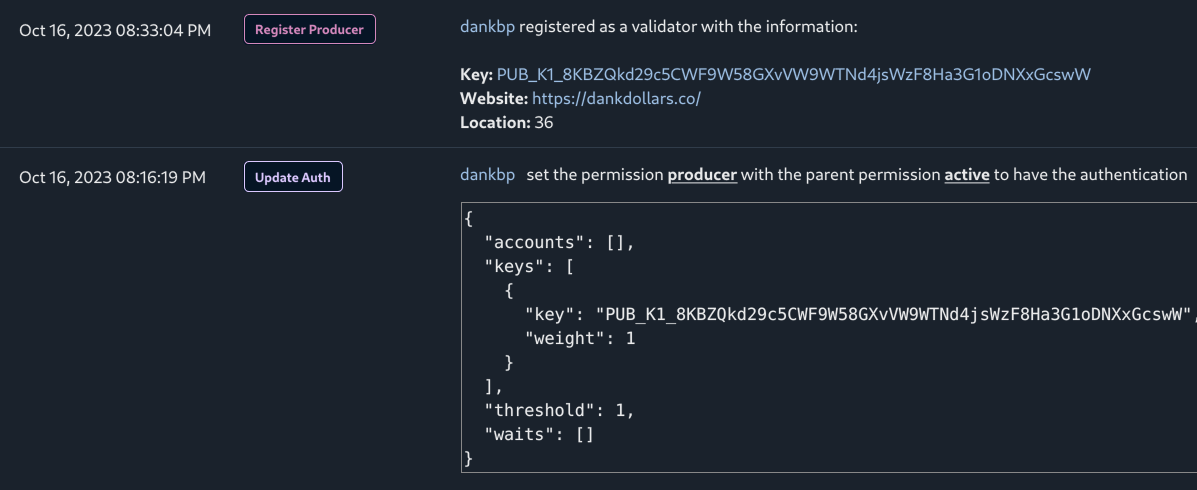
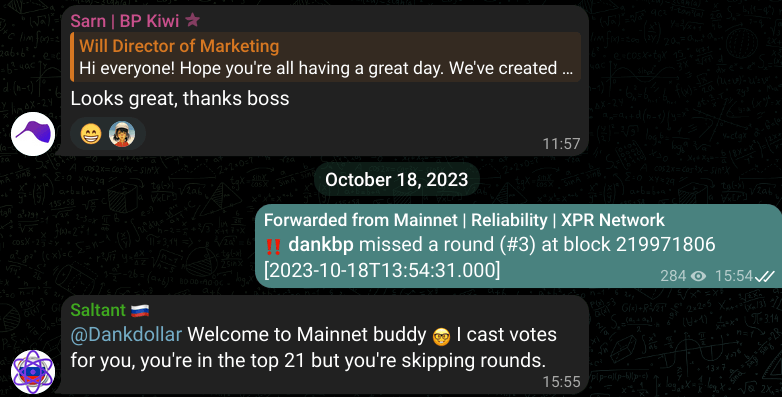
October 18, 2023 (15:54 UTC) – His BP (DankBP) entered into top21 and started to miss rounds. I informed him to investigate the issue with the node.
October 18, 2023 (16:40 UTC) – An hour later, he unregistered from the mainnet, changed the active key, and then registered the node using the updated active key.
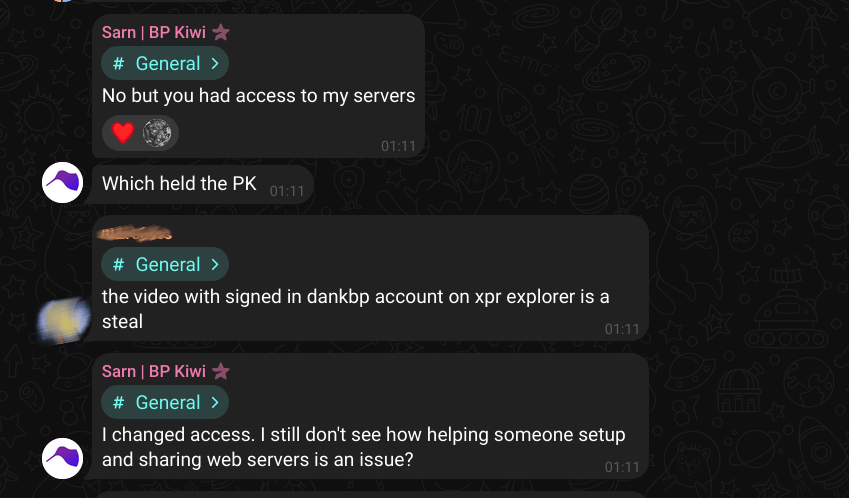
As per Sarn’s comment, it’s completely illogical. Why would “Troy” choose to change the active key in this specific scenario rather than doing so earlier?
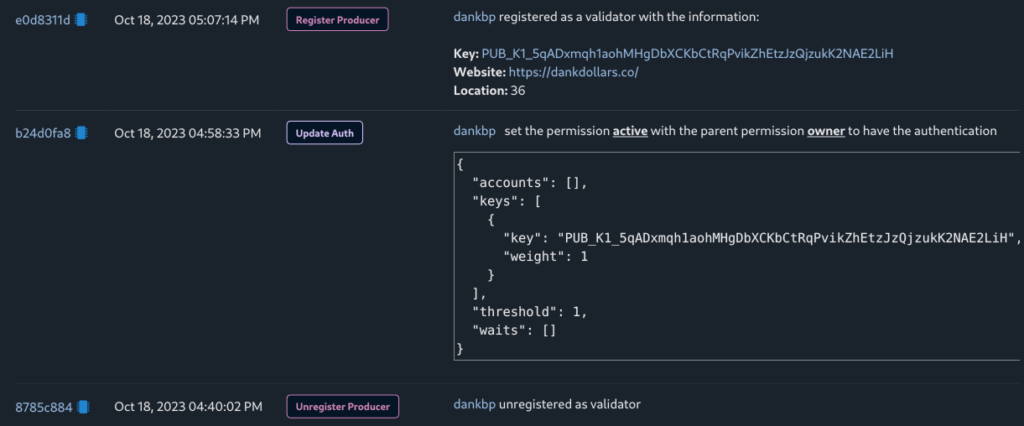
October 19, 2023 – I warned him to not use an active key in node registration.
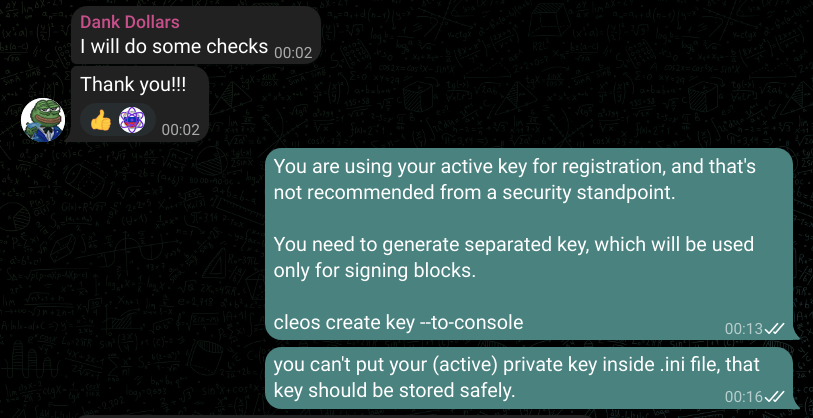
January 17, 2024 – After being exposed that he was running 2 BPs, he claimed that he changed keys. So he had access to those private keys since October 2, 2023 until October 18, 2023 for whole 16 days and later he changed active key, not to revoke or return access to “Troy”, but BECAUSE HE WAS MISSING ROUNDS and he thought that will solve the issue.
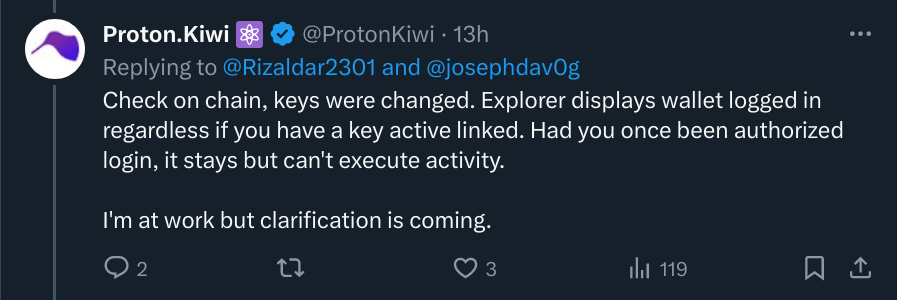
And a similar claim on the Telegram channel, but with an interesting detail where he said, “I changed access.” He didn’t say that “he (Troy)” changed access. The point here is that when people are truthful, they express themselves accurately, the opposite of being untruthful where you have to pay attention to every single detail to avoid exposing yourself. So, if Sarn changed access (keys), wouldn’t that mean Troy’s private key is no longer private?
https://t.me/XPRNetwork/1/948872
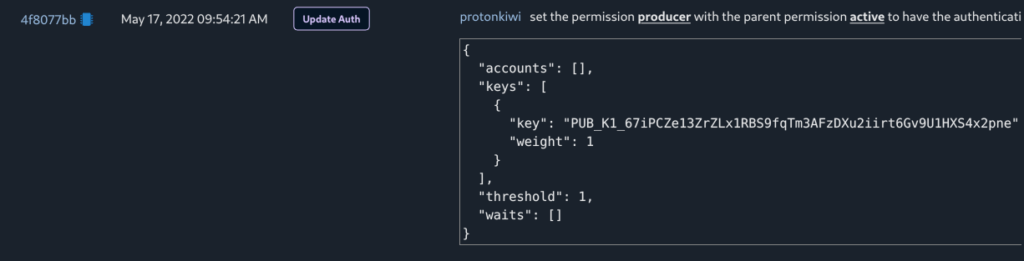
Now let’s take a look how ProtonKiwi registered as BP in May 17, 2022. He firstly created producer key:
Following that, on May 21, 2022, he registered on the mainnet using the producer key, repeating the same mistake made during the registration of DankBP.
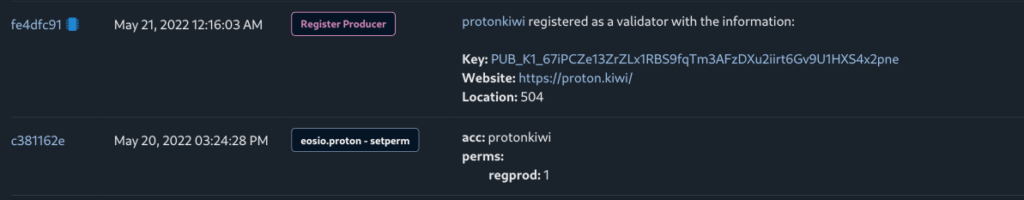
Indicating that both keys structure were setup by same pattern.
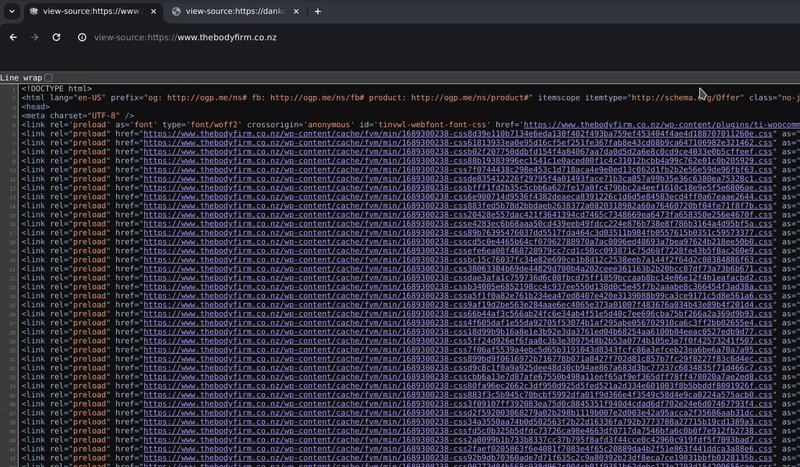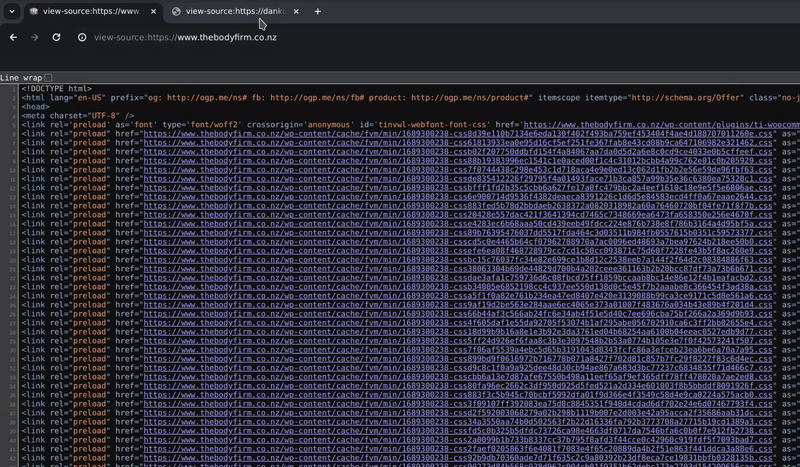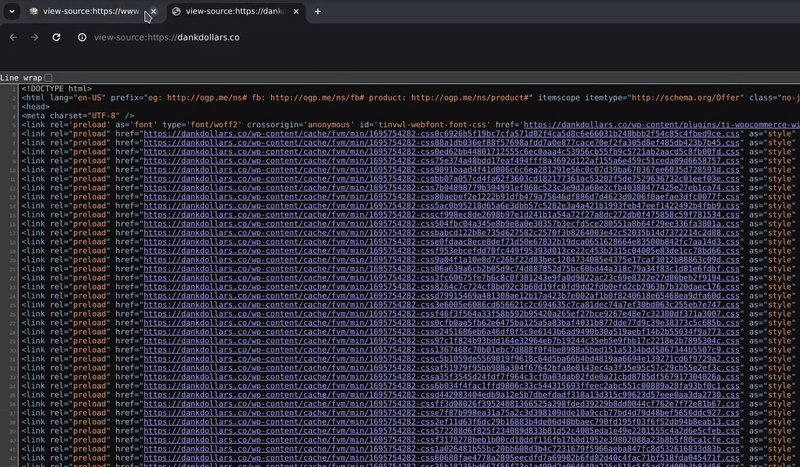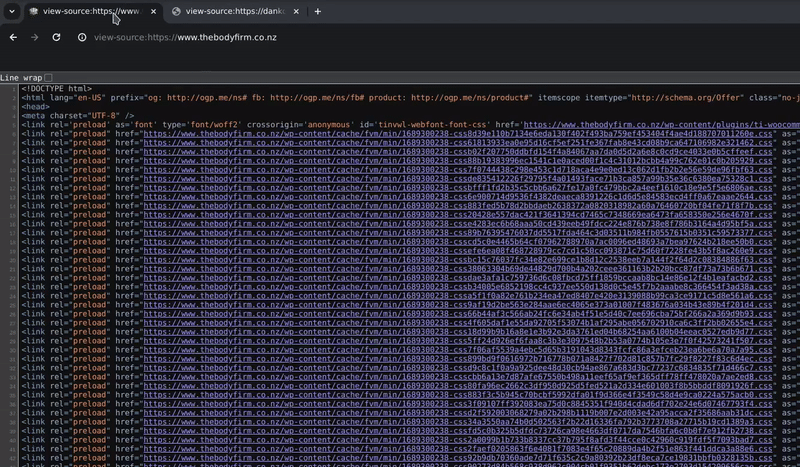
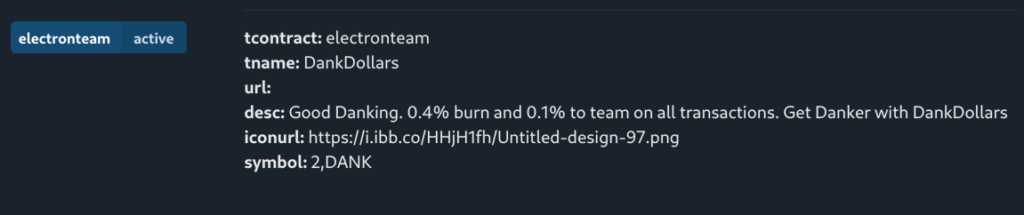
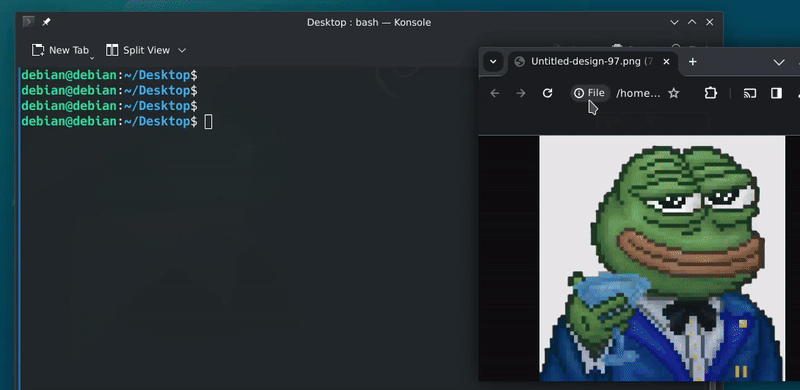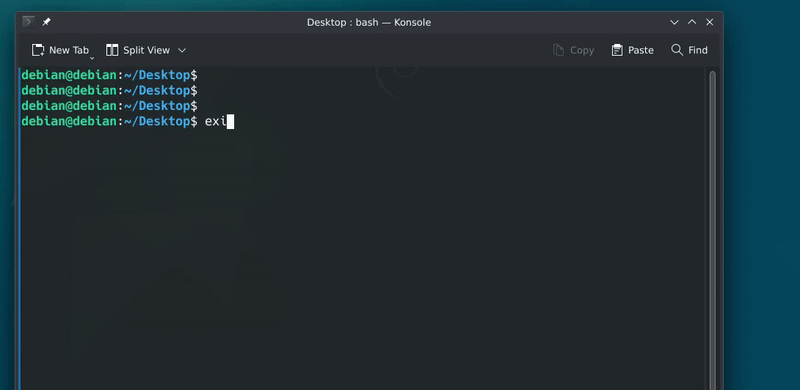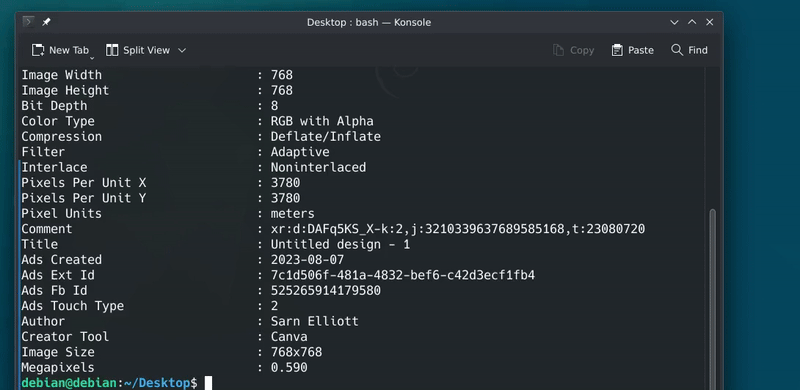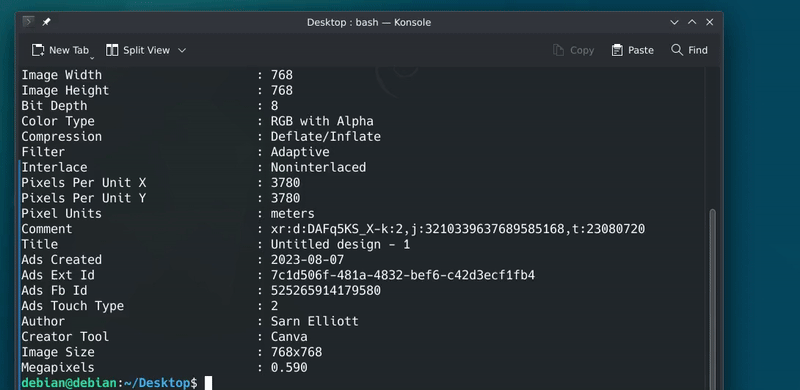
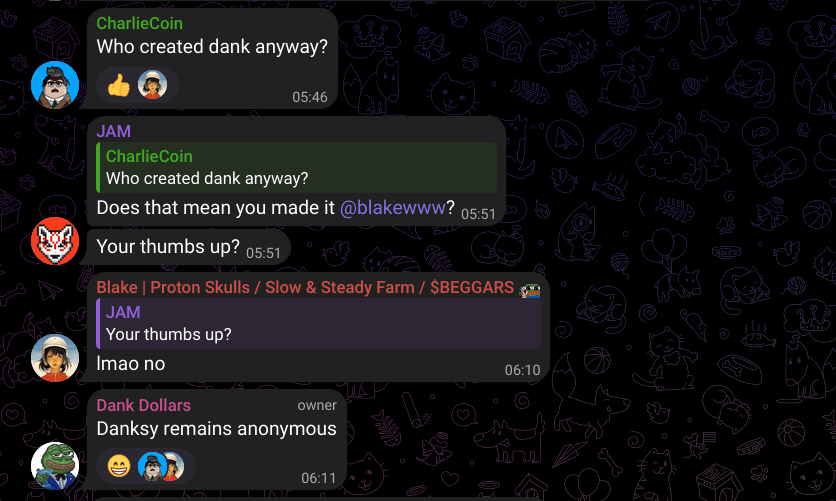
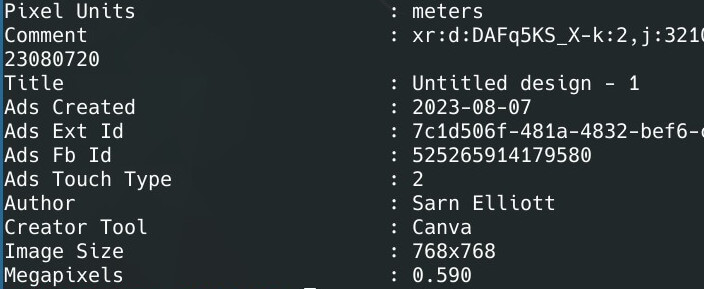
In X space, Sarn claimed that he did not mint the token. Despite the fact that the metadata of the token image used in the minting process explicitly indicates his involvement. Sarn clearly doesn’t understand that peace of evidence and its common use in forensic analysis.
Sarn is unaware that nearly every platform automatically removes metadata when sharing images with others. So the question here is; how he shared that image with Troy, and how it was used in the minting process?
(TX)
Ultimately, Sarn doesn’t feel any guilt for his actions, viewing the provided concrete evidence and details as mere assumptions.
More details will be uncovered in third part of this investigation.
Note: No information was obtained in an unethical way; all information used in this article is publicly available.