Secure/Multipurpose Internet Mail Extensions, or S/MIME, is an internet standard to digitally sign and encrypt email messages. It ensures the integrity of email messages remains intact while being received.
By using digital signatures, S/MIME provides for authentication, message integrity, and non-repudiation of origin. In addition, S/MIME includes encryption that strengthens privacy and data security for electronic messaging.
Signing Emails
S/MIME allows you to sign your emails to prove your identity as a legitimate business. Every time you create and sign an email, your private key applies your unique Digital Signature into your message. When your recipient opens your email, your public key is used to verify the signature. This ensures your recipient that the emails really came from you. Signing emails authenticates your identity in times where phishing attacks have already become so clever and it has become increasingly difficult to identify spoofed emails.
Free S/MIME Certificate
Actalis offers S/MIME certificates that are recognized on the most popular platforms and compatible with all the main S/MIME-compliant email applications, such as Microsoft Outlook, Mozilla Thunderbird, Exchange, Gmail, and many others.
Click here to validate your email and start a process to get free S/MIME certificate. Once you are done, you will get email with attachment and password for your newly generated certificate.
If you prefer to buy S/MIME certificate, then you can purchase from Sectigo.
Now it’s time to import into Thunderbird. Open Settings and then navigate to End-To-End Encryption, where you will be able to choose your S/MIME certificate for digital signing.
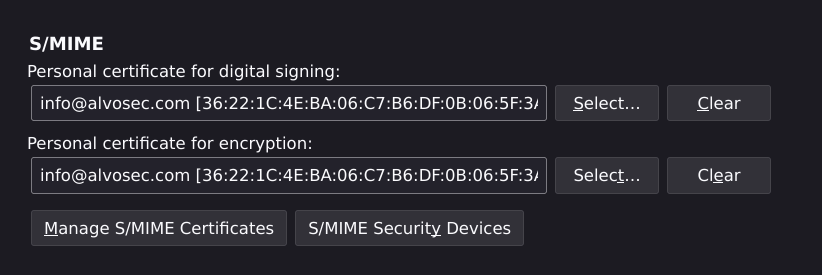
It’s time to test. Send email by choosing S/MIME tab where it says Digitally Sign. Once email is sent the recipient will be able to verify identity of sender.
If you click on Sender info, you will get more information about digital signature.
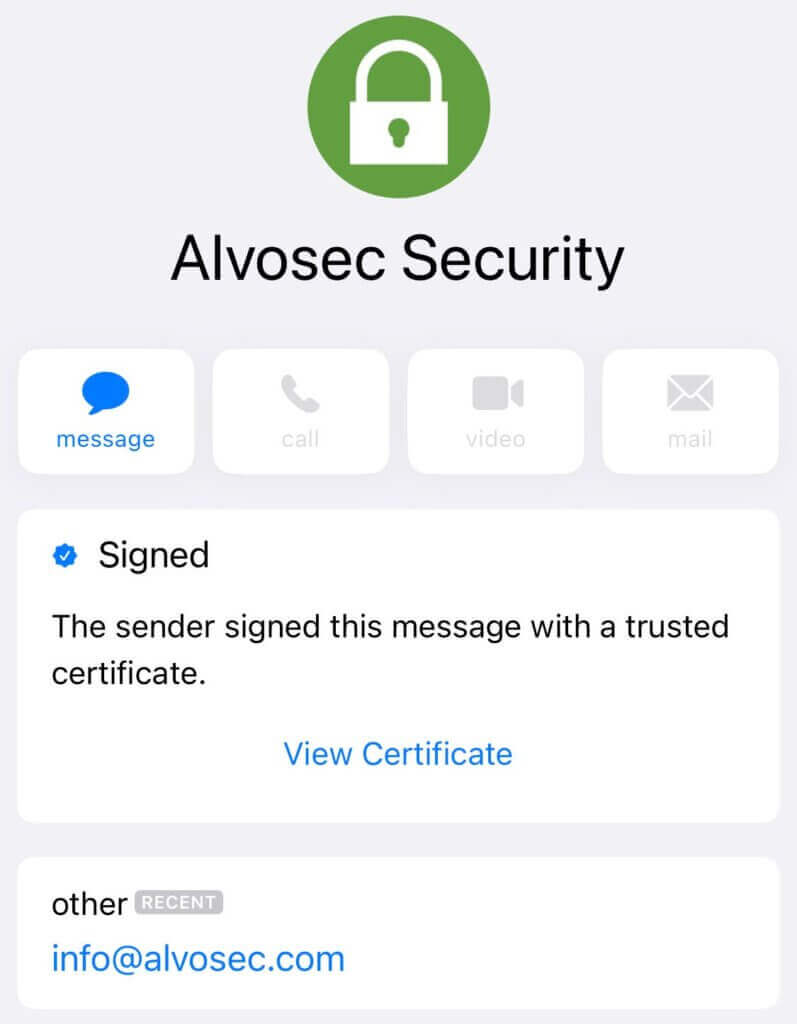
This means that message integrity and sender authenticity are verified.
S/MIME digital signatures safeguard against email spoofing by verifying the sender’s identity, ensuring the message contents have not been changed and confirming the sender actually sent the message.