Ethereum co-founder Vitalik Buterin’s account on X (formerly Twitter) was compromised late at night on Sept. 9. Vitalik’s hacked account was used to promote a domain that hosted drainer which was designed to steal crypto and non-fungible tokens (NFTs) from wallets that interacted with it. According to latest data, the hacker has drained around $691,000 of assets from victims.
The method through which the attackers gained access to Vitalik's account remains undisclosed. However, our primary concern should be understanding how these attackers executed the attack. Many cryptocurrency news websites have not yet analyzed this, and consequently, users may not comprehend how to defend against such attacks in the future unless we provide explanations.
Below is a screenshot of the malicious post that was promoted during the attack. What's particularly noteworthy is that the embedded link appeared legitimate: https://consensys.io/
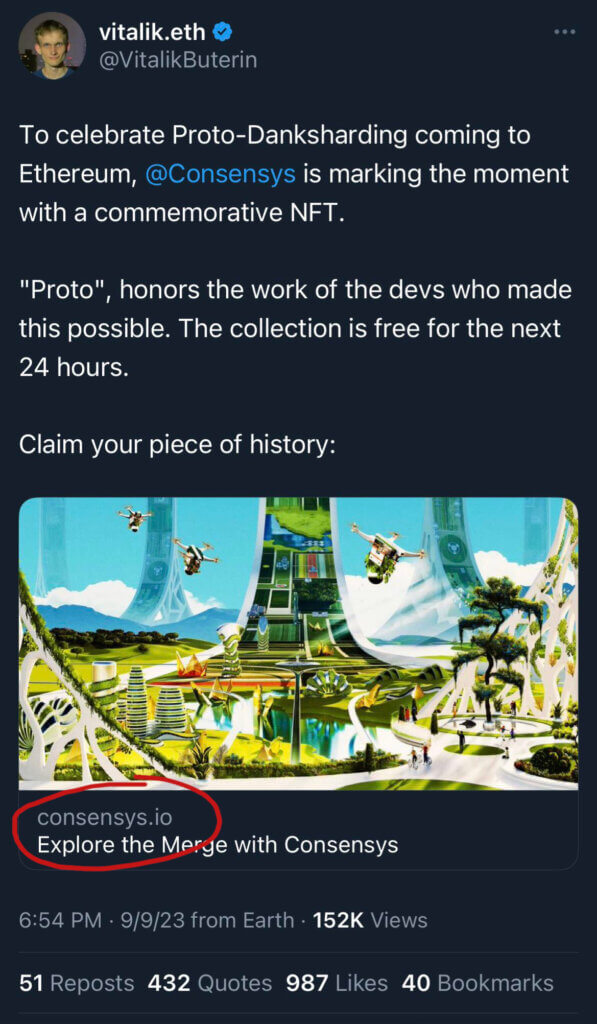
Google search result of consensys.io:

Surprisingly, this website was not a phishing domain. However, when a user clicked on this embedded post, it redirected them to consensys.fi.
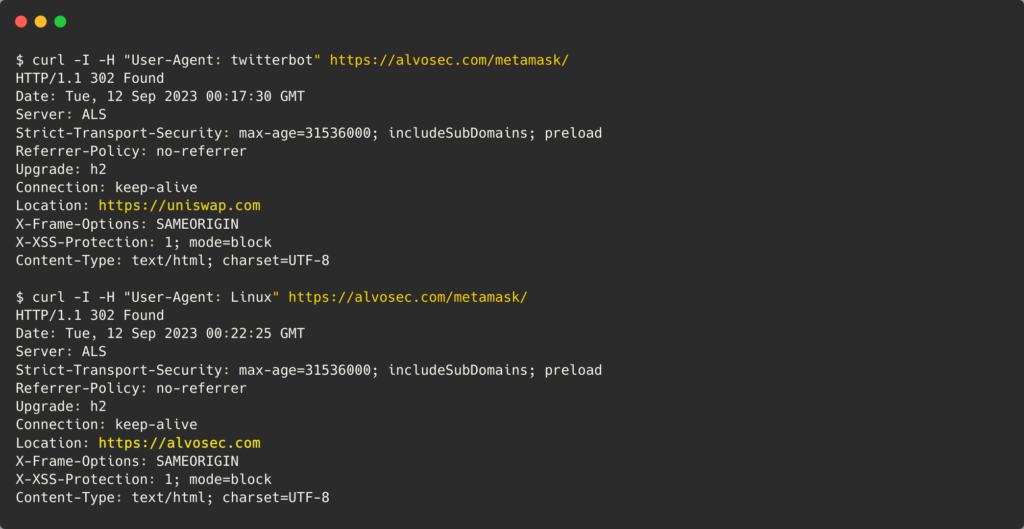
The attacker spoofed the embedded URL as a x (Twitter) card, assigning various destinations depending on the user-agent.
When X attempts to embed and generate a post card with a preview image, it verifies the location of the posted URL. What we've created is a script that identifies the User-Agent crawling that page and responds with a distinct location, as shown in the image below.
This means that when we post our URL: https://alvosec.com/metamask on X it will create preview such as this one:
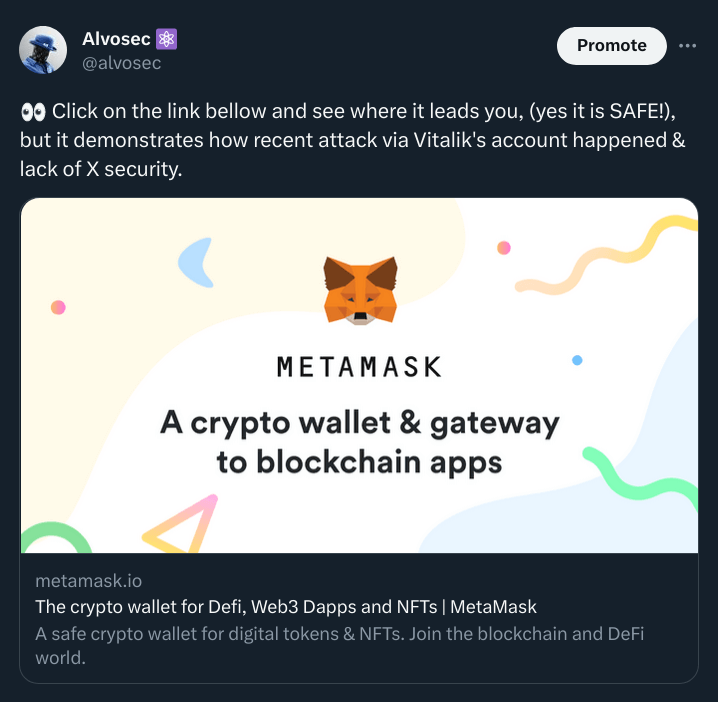
X post is available here.
But when user clicks on this link it will lead him to https://alvosec.com/ and not on https://metamask.io/.
Now let's go back to Vitalik case, what we know so far is that attackers purchased these 3 domains:
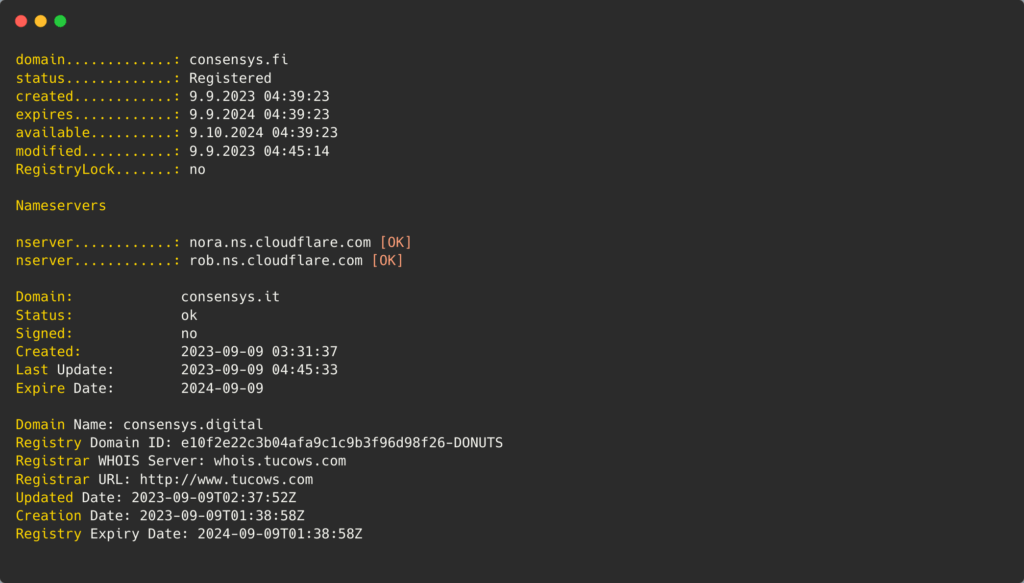
Because the post was quickly removed, we couldn't thoroughly examine all the redirects that occurred upon clicking. It's possible that the attackers set up a host to act as proxy, guiding users to one of the three domains. This could have been a backup plan in case one of the domains was blocked due to user reports.
Once again, this underscores the severity of attacks within the cryptocurrency community, often concealing their true intentions. We strongly recommend that all users use one of our tools, https://xprotect.org/scan, to scan any website before linking their wallet to it. In this particular case, scanning these domains using our tool would have yielded a remarkably low trust score. Firstly, because all domains were hosting malicious files (drainer), and secondly, because they all fell into the NRD category, indicating that newly registered domains typically have very low trust scores.