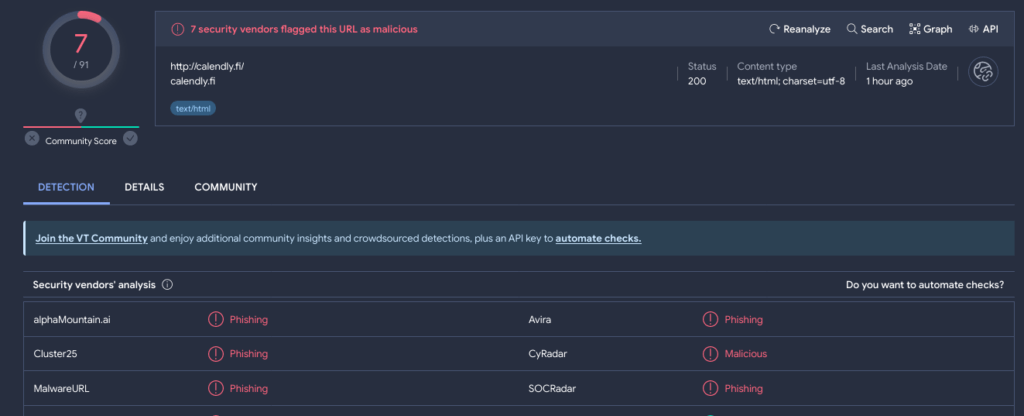
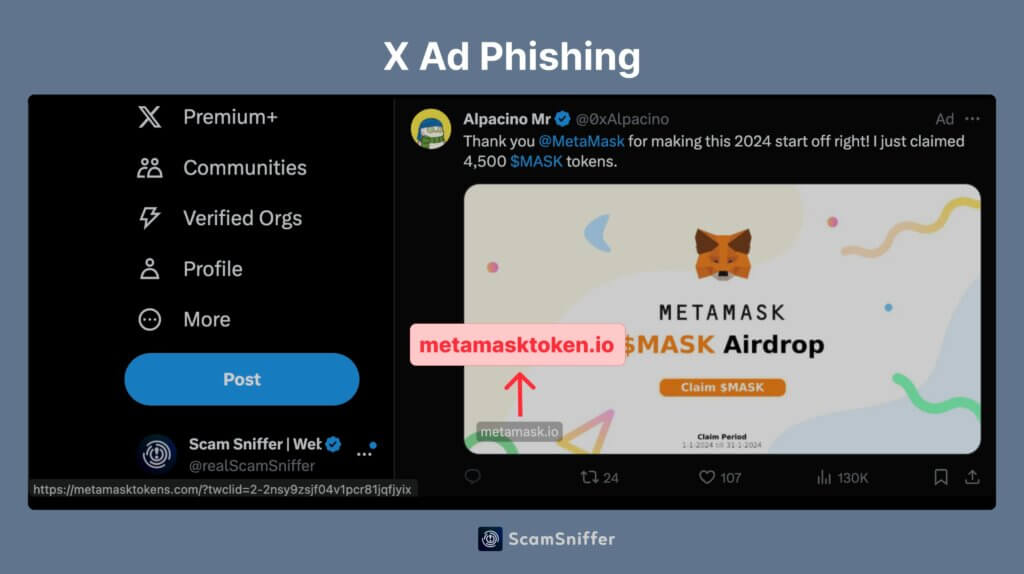
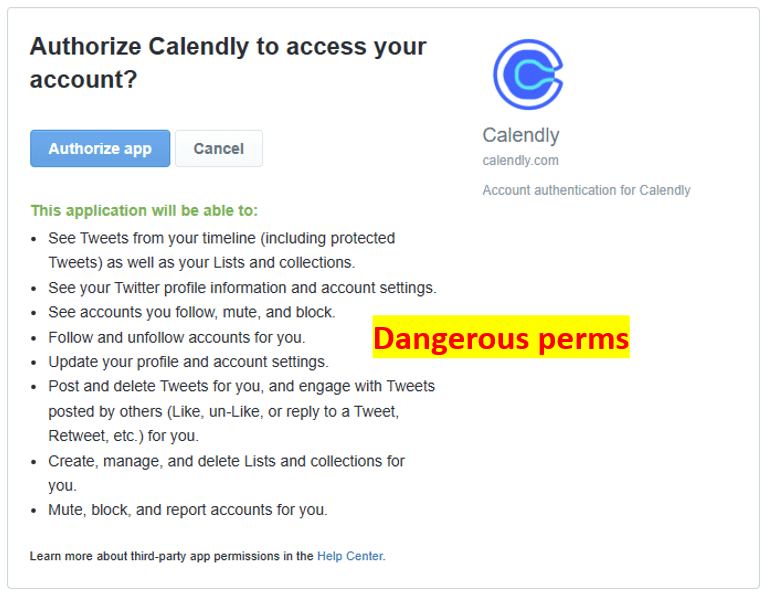
In today’s digital age, scams and hacks have become increasingly sophisticated, preying on unsuspecting internet users. From phishing emails to AI-powered scams, online threats lurk around every corner, ready to exploit vulnerabilities in our psychological defenses. To safeguard yourself effectively, it’s crucial to adopt a skeptical mindset and employ simple yet effective strategies to thwart these manipulative tactics.
Understanding Psychological Manipulation
Psychological manipulation lies at the heart of most online scams and hacks. These tactics are designed to exploit human emotions, cognitive biases, and tendencies, making us more susceptible to falling victim. Whether it’s fear, greed, curiosity, or urgency, scammers know how to push the right buttons to manipulate our behavior.
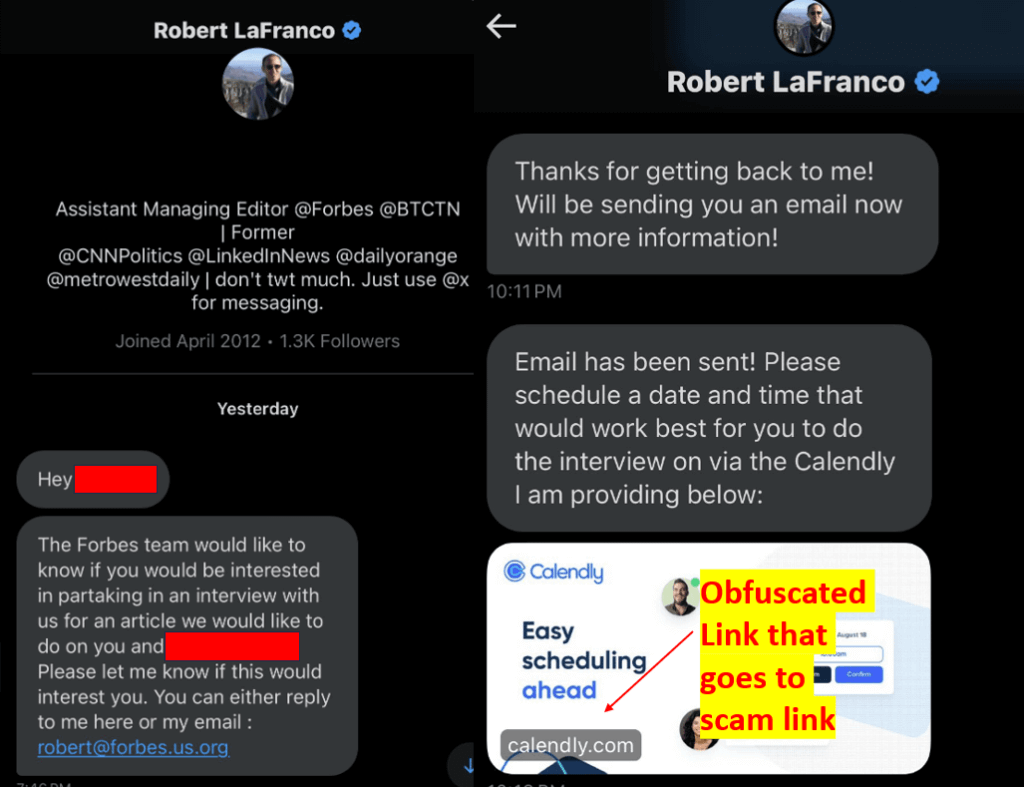
One common tactic is urgency. Scammers create a sense of urgency to pressure victims into making impulsive decisions without thorough consideration. They often use phrases like “Act now!” or “Limited time offer!” to compel users to act hastily, bypassing their rational judgment.
Another tactic is authority. Scammers may impersonate trusted entities, such as banks, government agencies, or well-known companies, to lend credibility to their schemes. By posing as someone in a position of authority, they aim to disarm skepticism and convince victims to comply with their demands.
Furthermore, exploiting social proof is another effective strategy. Scammers leverage social influence by showcasing fabricated testimonials, fake reviews, or inflated statistics to create a false sense of trustworthiness. Seeing others seemingly benefiting from the scam can persuade individuals to follow suit.
Simple Rules to Stay Safe
- Question Everything: Adopt a healthy skepticism towards unsolicited emails, messages, or offers, especially those that evoke strong emotions or demand immediate action. Take a moment to pause and evaluate the legitimacy of the request before responding or clicking on any links.
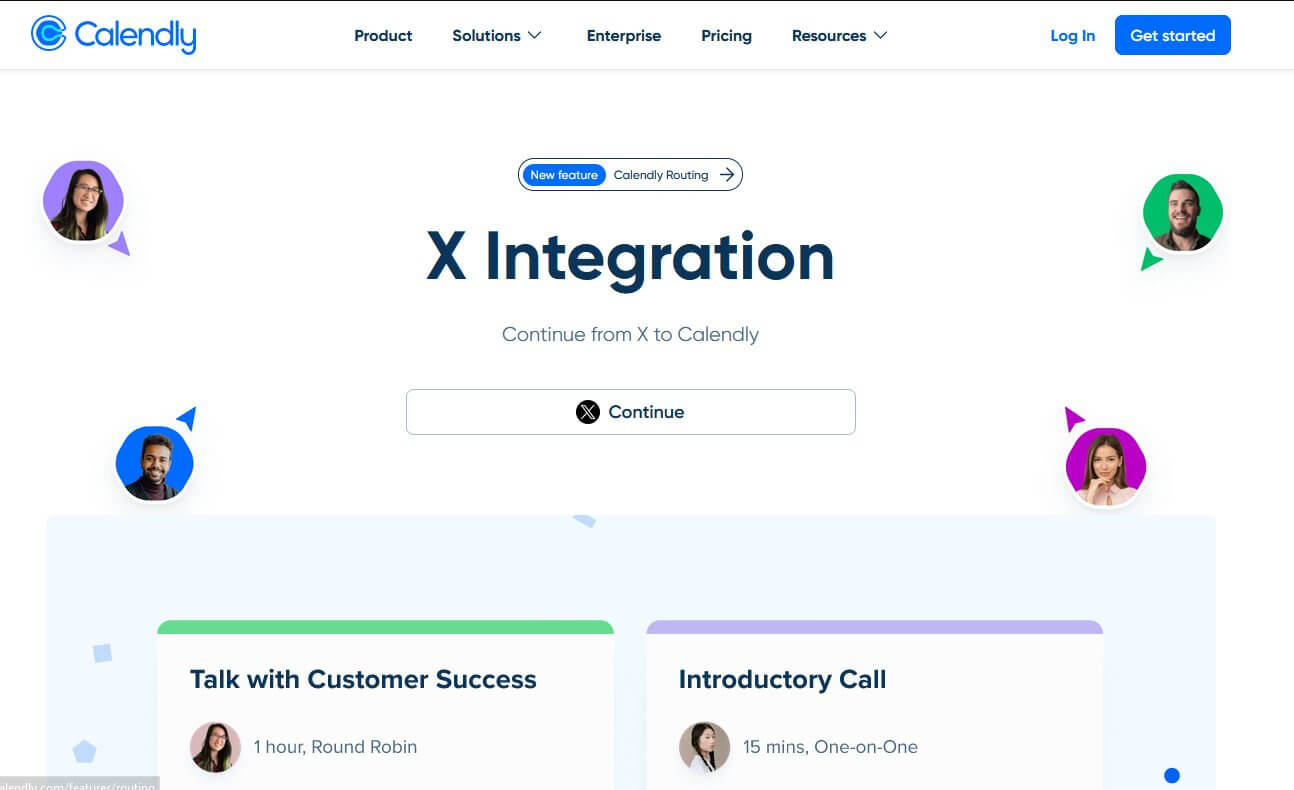
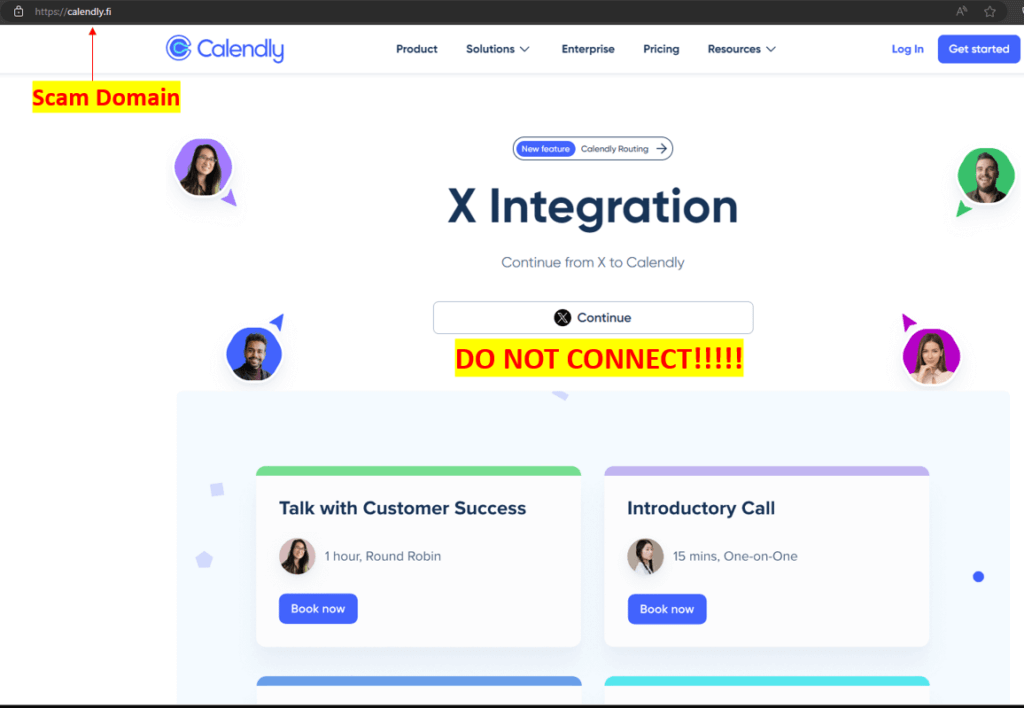
- Verify the Source: Before divulging any personal information or engaging with an online offer, verify the legitimacy of the sender or website. Look for signs of authenticity, such as official email addresses, secure website connections (https://), and contact information. When in doubt, reach out to the supposed sender through official channels to confirm the authenticity of the communication.
- Guard Your Personal Information: Be cautious about sharing sensitive information online, such as passwords, financial details, or personal identifiers. Legitimate organizations will never request such information via unsolicited emails or messages. Refrain from providing personal data unless you’ve initiated the interaction and trust the recipient implicitly.
- Stay Informed: Keep yourself updated on the latest online scams and hacking techniques. Regularly educate yourself about common red flags, emerging threats, and best practices for online security. By staying informed, you’ll be better equipped to recognize and avoid potential pitfalls.
- Use Security Measures: Implement robust security measures to protect your devices and accounts from unauthorized access. This includes using strong, unique passwords for each online account, enabling two-factor authentication whenever possible, and keeping your software and antivirus programs up to date.
- Trust Your Instincts: If something feels off or too good to be true, trust your instincts and proceed with caution. Don’t let fear of missing out or the promise of a quick reward cloud your judgment. Take the time to research and validate any suspicious claims before taking action.
Summary
In the digital landscape rife with scams and hacks, safeguarding your online security requires a combination of vigilance, skepticism, and informed decision-making. By understanding the psychological tactics employed by manipulative actors and adhering to simple yet effective rules, you can significantly reduce your risk of falling victim to online scams and protect your sensitive information from exploitation. Stay alert, question everything, and prioritize your online safety above all else.