Hashcat is a password recovery tool that uses brute-force or dictionary attacks to recover passwords from hashes. It is a popular tool among cybersecurity professionals and researchers, as it is capable of cracking a wide variety of hashes and supports many different algorithms.
Hashcat is a powerful tool for cracking various types of hashes and can be used to recover password-protected zip files, documents, and WPA .pcap files. It supports over 250 different encryption modes and offers features like mask attacks, which allow users to customize their attacks. Hashcat is easy to use and can decrypt hundreds of hash types in just a few steps. It is also a multi-platform tool.
To use Hashcat, you will need to obtain a hash of the password you wish to crack and then run Hashcat with the appropriate options to perform the cracking process. Hashcat supports a wide range of options and algorithms, so it is important to familiarize yourself with the tool and its documentation before attempting to use it.
To install it in Ubuntu / Debian-based systems, use the following command:
apt install hashcat
Once the installation is done, we can check Hashcat’s help menu using this command:
hashcat -h
Now that we know what hashing and Hashcat are, let’s start cracking some passwords.
Let’s create two hashes: A MD5 hash and a SHA1 hash for the string "password".
MD5 hash -> 5f4dcc3b5aa765d61d8327deb882cf99
SHA1 hash -> 5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8
We can store these hashes under the names md5.txt and sha1.txt to use them when working with Hashcat.
To crack a password using Hashcat, here is the general syntax.
hashcat -m value -a value hashfile wordlist
Let’s dissect the syntax. We have used two flags, -m and -a . The -m flag is used to specify the hash type and the -a flag is to specify the attack mode. You can find the list of hash types and attack modes here.
Attack modes:
0 = Straight
1 = Combination
3 = Brute-force
6 = Hybrid Wordlist + Mask
7 = Hybrid Mask + Wordlist
Straight Attack, also known as a dictionary or wordlist attack.
Combinator Attack involves the combination of two wordlists to obtain a password guess.
Brute-force Attack Brute-force attacks use masks (built-in charsets) to set the range and type of characters to be combined and used for attacks. The image below show the masks. Masks are more efficiently used after some sort of social engineering or if you have an idea of what the password could look like.
? | Charset
===+=========
l | abcdefghijklmnopqrstuvwxyz
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ
d | 0123456789
h | 0123456789abcdef
H | 0123456789ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
a | ?l?u?d?s
b | 0x00 - 0xff
Mask attack is a type of password cracking technique that allows you to specify a pattern for the password being sought, rather than providing a list of possible passwords to try. This can be particularly useful when you have some information about the structure of the password but not the actual password itself.
For example, suppose you know that the password is 8 characters long and consists of only lowercase letters and numbers. You could specify a mask of "?l?l?l?l?l?l?l?l" to tell hashcat to try all possible combinations of 8 lowercase letters and numbers. This can be much more efficient than trying all possible combinations of 8 characters, because it reduces the search space by only considering passwords that match the specified pattern.
To use a mask attack in hashcat, you would specify the "-a 3" option followed by the mask pattern. For example:
hashcat -a 3 ?l?l?l?l?l?l?l?l hash.txt
This would tell hashcat to perform a mask attack using the specified mask pattern, and to try to crack the hashes in the "hash.txt" file.
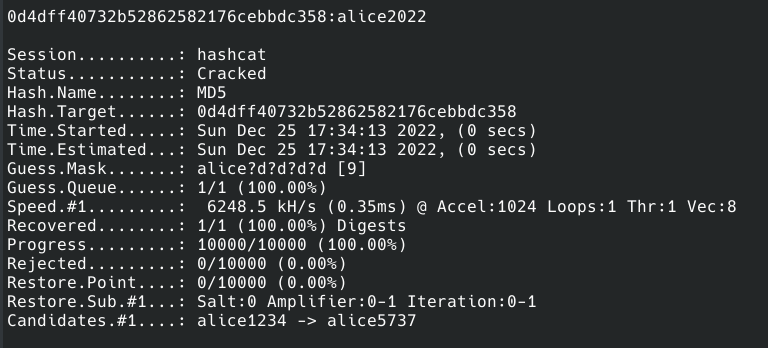
Note that you can also specify possibly known characters of password, so if you remember that password was started with "alice" but you forgot for example the year or number after that password, you can use following command:
hashcat -m 0 hash.txt -a 3 alice?d?d?d?d --force
Hashing is a technique used to secure data, such as passwords, by converting it into a random string using a mathematical function. This function is irreversible, meaning that the original data cannot be obtained from the generated string. Hashcat is a tool that can be used to try to recover the original data by attempting to crack the generated string, also known as a hash.