Lazarus, a notorious hacking group, has launched a new campaign called "Operation DreamJob," targeting Linux users with malware for the first time. This recent attack was detected by ESET's researchers and confirms with a high degree of certainty that Lazarus was responsible for the recent supply-chain attack on VoIP provider 3CX.
Operation DreamJob is a social engineering attack that tricks software and DeFi platform employees with fake job offers on LinkedIn or other social media platforms. When victims download the malicious file, disguised as a job offer document, malware is dropped onto their computer.
In the case discovered by ESET, Lazarus used a spearphishing or direct message approach to distribute a ZIP archive named "HSBC job offer.pdf.zip" that contained a Go-written Linux binary. The malware used a Unicode character in the file name to appear as a PDF, with the apparent dot character in the filename represented by the U+2024 Unicode character. This trick is an attempt to deceive the file manager into treating the file as an executable instead of a PDF. Consequently, when a user clicks on the file, the malware launches and displays a decoy PDF while simultaneously downloading a second-stage malware payload from a private repository hosted on the OpenDrive cloud service.
We've written simple bash script that can detect if a filename contains the leader dot U+2024.
#!/bin/bash
for file in *; do
if [[ "$file" =~ "․" ]]; then
echo "Found leader dot in filename: $file"
echo "Hex value of leader dot: $(echo -n "․" | od -t x1)"
echo "Position of leader dot in filename: $(expr index "$file" "․")"
fi
done
This script uses a regular expression to check if the filename contains the U+2024 character, and if it does, it will print details about the character, including its hexadecimal value and its position in the filename.
The decoy PDF displayed to the target (ESET)
The second-stage payload is a C++ backdoor called "SimplexTea," which is dropped at "~/.config/guiconfigd. SimplexTea." Additionally, OdicLoader modifies the user's ~/.bash_profile to ensure that SimplexTea is launched with Bash, and its output is muted whenever the user starts a new shell session.
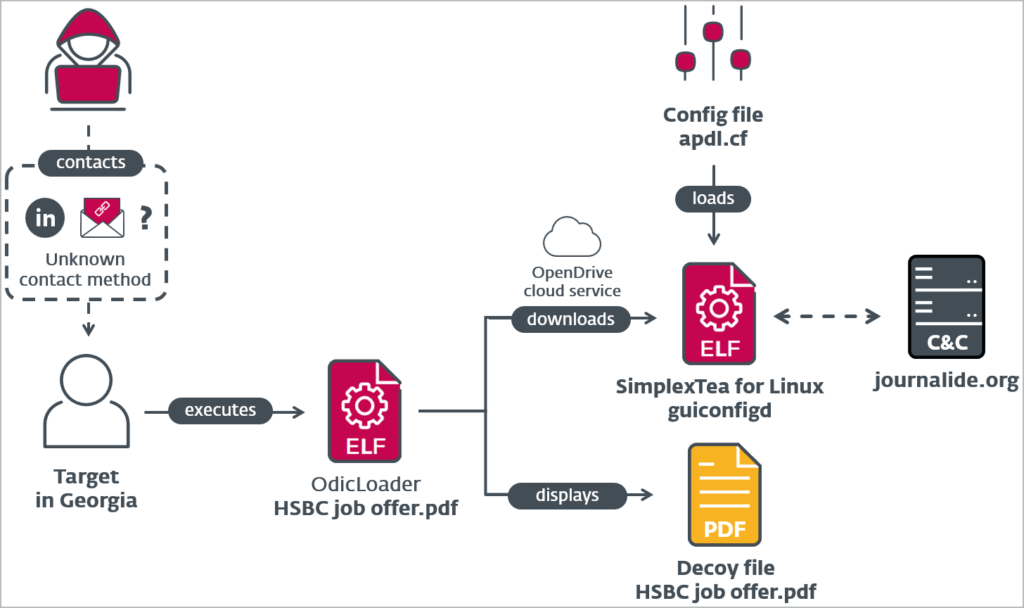
SimplexTea is a backdoor designed for Linux and coded in C++. The names of the classes bear a strong resemblance to the function names that were uncovered in a file named sysnetd. This file was uploaded to VirusTotal from Romania and can be identified by its SHA-1 hash value of F6760FB1F8B019AF2304EA6410001B63A1809F1D. Due to the similarities between the class and function names of SimplexTea and sysnetd, it is speculated that SimplexTea is a newer iteration of sysnetd and has been rewritten from C to C++.