The rise in popularity of cryptocurrencies has encouraged cybercriminals to find innovative ways to attack markets, users and any structure where cryptocurrencies are stored. In simple words, if an attacker is able to exploit some area of a chain, smart contract, exchange or illegitimately withdraw cryptocurrency, it would be deemed as a hack or stealing. Scammers around the world took home a record of $14 billion in cryptocurrency in 2021.
Phishing scams don’t make up a huge percentage of bitcoin scams, but the Ledger phishing scam was notable. Ledger provides hardware wallets, devices on which users store cryptocurrency. After user email addresses were leaked in a data breach (disclosed in July 2020), a subsequent October phishing scam targeted customers involved in the breach.
Emails sent to victims contained a link leading to a phishing site that looked like the legitimate Ledger website. In turn, the website contained a link that actually downloaded malware capable of draining the victim’s Ledger wallet. Chainalysis has identified more than €3 million worth of stolen funds related to the scheme. Source
After we identified that cloned and fake Telegram group is trying to steal private keys from different wallets, we began our investigation.
At first stage we gathered all available information from their infrastructure, all related domains, servers, emails, DNS, hosting accounts and the rest of what we thought it's valuable for further analysis. At second stage we tried to establish communication with them. As you may already know, they are not hard to find and if you don't find them, they will find you.
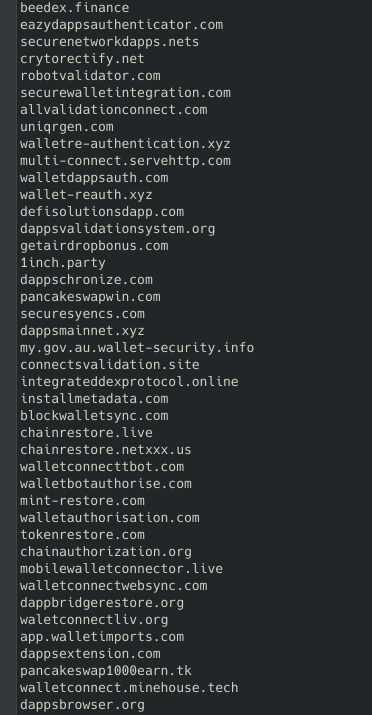
List of all domains that were related to this organized fraud.
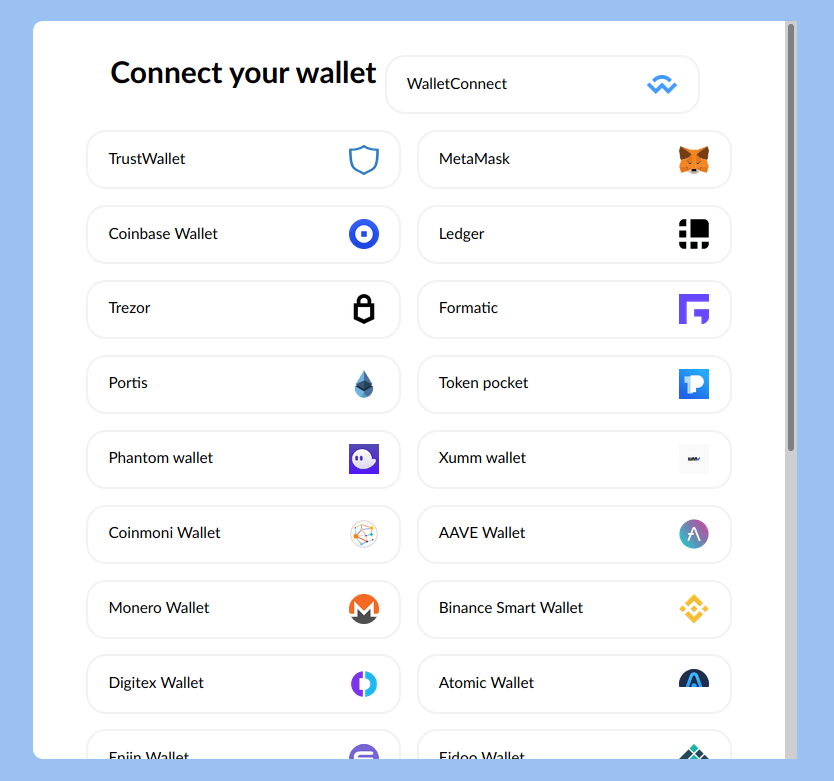
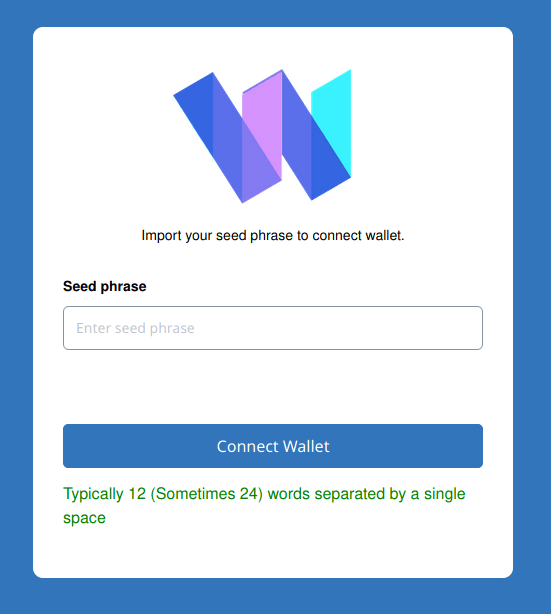
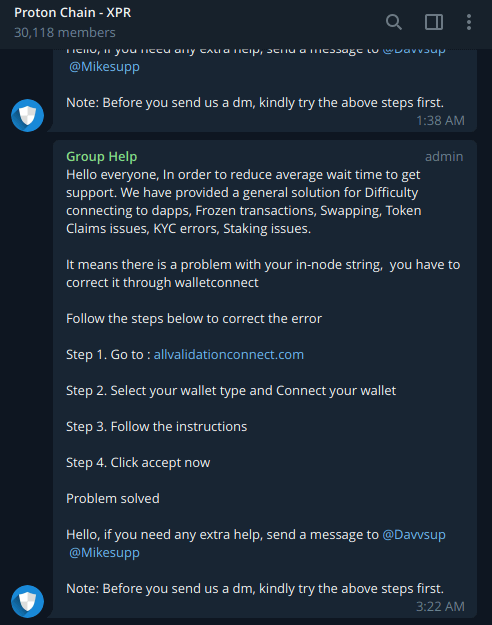
While communicating with them, we used some of social engineering tricks, where we pretended to have a problem with our wallet. They immediately responded with their scam website and instructed us to enter our 12 words phrase or private key in order to solve problem with wallet.
Here is an example of fraudulent website.
We continued with our pretending that something went wrong and we were not able to proceed, because their shitty website is keep redirecting us on Google, so we gave them a potential 'solution' for our 'problem'.
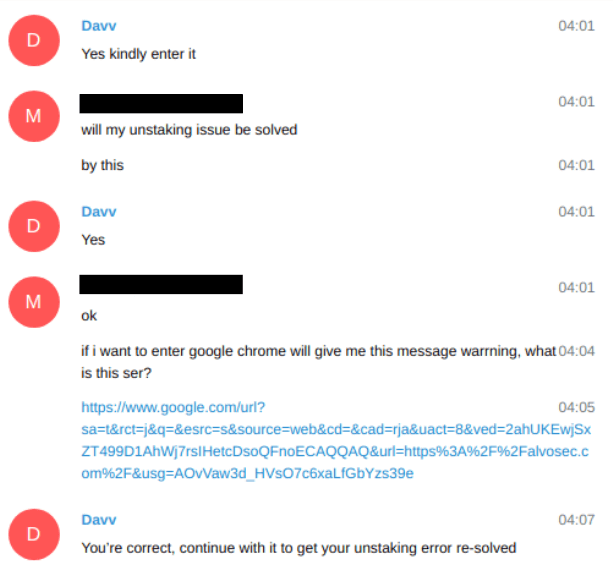
This (legit) Google URL silently redirected them on our page, where we captured their information. Locations were different from Nigeria, USA etc. Not to mention how mad they were after realizing that they didn't open Google.com but Alvosec.com. One of them even used abusive language against us. : )
Chatting with them was kinda boring, so we went for real action. By analyzing their websites we again found valuable information, access logs, vulnerabilities, easy access to their mostly used shared hosting accounts.
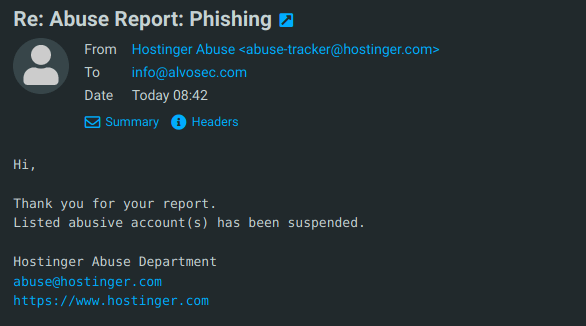
Done, we had enough and didn't want to waste more time on them, so we bulk reported all confirmed scam websites. We were positively surprised, most of the reported websites were shut down and the one from the group was suspended only after three hours hxxp://allvalidationconnect.com/ .
Never click on suspicious or malicious links, when you click on unverified links or download suspicious apps you increase the risk of exposure to malware.
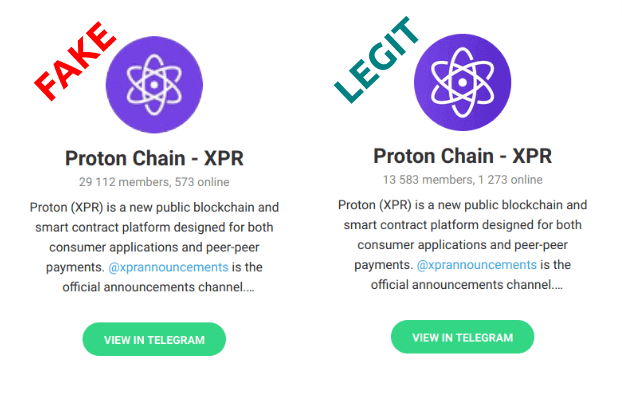
This Telegram group is fake and we are hoping that it will be soon suspended. The only real one and official is this one - https://t.me/protonxpr
Most of the time reporting abusive domain name(s) is complicated, so we are planning to automate process of bulk reporting. If anyone is interesting, there are already interesting projects for reporting https://phish.report/ and https://www.abuseipdb.com/bulk-report.
Remember, there are more sophisticated attacks, scams out there, so act responsibly and carefully.
If you want to report a domain name, email address or IP address involved in abusive activity, here are some tips to follow to make this process easier.
Always submit full information such as domain name, full email - forward as attachment (.eml), IP addresses. Don't submit chat messages from Discord, Telegram etc., unless there is some valuable information that can improve our future investigations.
All reports send on this email: report@alvosec.com.