Kaspersky analysts have issued a warning about a surge of trojanized Tor Browser installers that are infecting users in Russia and Eastern Europe with clipboard-hijacking malware. This type of malware steals cryptocurrency transactions from infected users. Although this attack is not new or innovative, it remains effective and widespread, affecting many users globally.
While these malicious Tor installers target users in countries around the world, Kaspersky highlights that most of the attacks are aimed at Russia and Eastern Europe. Kaspersky believes that this is due to the ban of the Tor Project's website in Russia at the end of 2021, which was confirmed by the Tor Project itself.
According to the Tor Project, Russia was the second-largest country in terms of the number of Tor users in 2021, accounting for over 300,000 daily users or 15% of all Tor users.
The Tor Browser is a specialized web browser that provides users with anonymity by concealing their IP address and encrypting their web traffic. Additionally, Tor can be used to access onion domains, also known as the "dark web," which cannot be indexed by regular search engines or accessed through standard browsers.
Cryptocurrency holders may use Tor to transact with cryptocurrencies anonymously or to access illegal dark web market services that only accept payments in cryptocurrency.
To deceive users, Trojanized Tor installations are often marketed as "security-enhanced" versions of the official Tor Project vendor or distributed in countries where Tor is banned, making it difficult to download the official version.
Kaspersky has found that these installers include a standard version of the Tor browser, which is often outdated, and an additional executable hidden inside a password-protected RAR archive set to extract automatically on the user's system. Furthermore, the installers have localized names such as 'torbrowser_ru.exe' and offer language packs for users to choose from.
The malware is extracted from the archive in the background and executed as a new process while also being registered on the system autostart, while the standard Tor browser is launched in the foreground. The malware also employs a uTorrent icon to conceal itself on the compromised system.
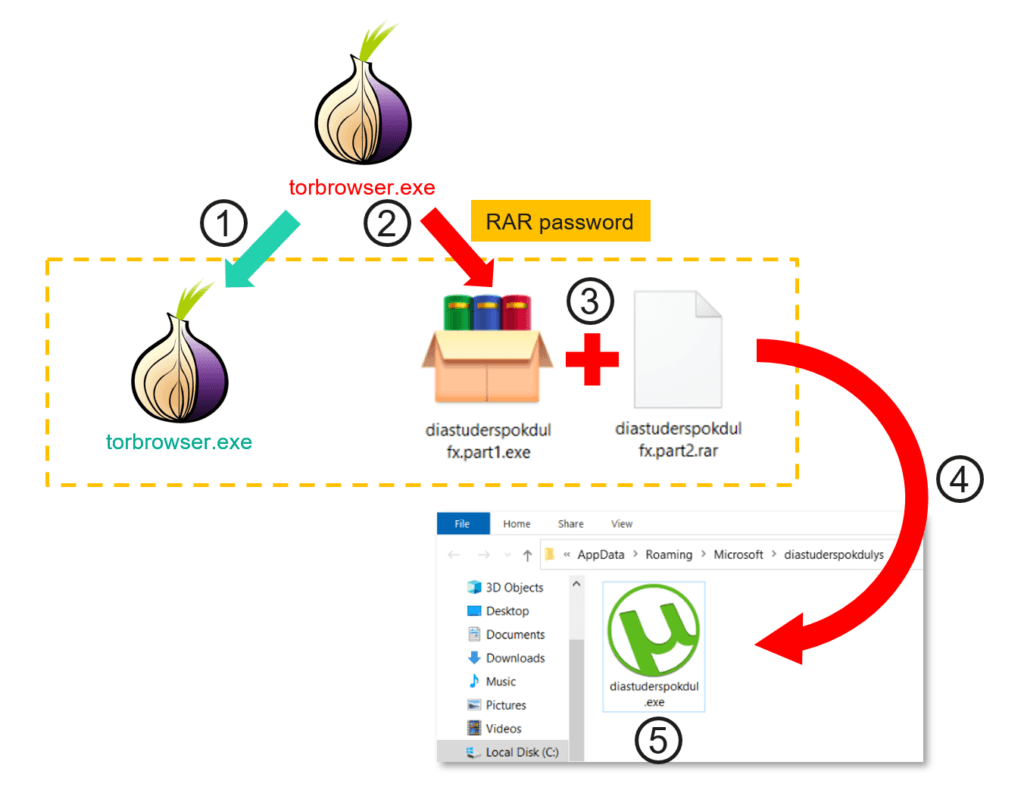
The victim downloads Tor Browser from an unofficial source and opens it as torbrowser.exe. However, the installer lacks a digital signature and is merely a RAR SFX (self-extracting executable) archive that contains three files:
Due to the complexity of cryptocurrency addresses, it's common practice to copy and paste them instead of manually typing them out. The malware uses regular expressions to scan the clipboard for recognizable crypto wallet addresses and replaces them with associated cryptocurrency addresses that belong to the attackers. As a result, when the user pastes the address, the attacker's address is pasted instead, enabling them to steal the sent transaction.
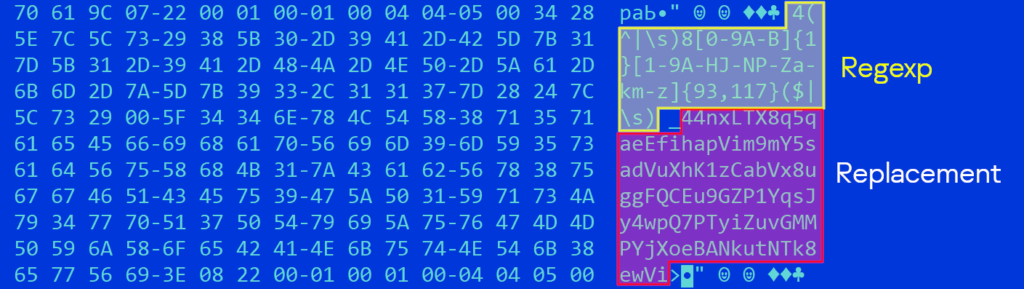
Hexdump of the malware data with regular expressions and replacement wallet IDs
We identified the following regular expressions inside the sample.
bc1[a-zA-HJ-NP-Z0-9]{35,99}($|\s) – Bitcoin
(^|\s)[3]{1}[a-km-zA-HJ-NP-Z1-9]{25,34}($|\s) – Litecoin/Bitcoin Legacy
(^|\s)D[5-9A-HJ-NP-U]{1}[1-9A-HJ-NP-Za-km-z]{32}($|\s) – Dogecoin
(^|\s)0x[A-Fa-f0-9]{40}($|\s) – ERC-20 (i.e. Ethereum, Tether, Ripple, etc)
(^|\s)[LM]{1}[a-km-zA-HJ-NP-Z1-9]{25,34}($|\s) – Litecoin Legacy
((^|\s)ltc1[a-zA-HJ-NP-Z0-9]{35,99}($|\s) – Litecoin
(^|\s)8[0-9A-B]{1}[1-9A-HJ-NP-Za-km-z]{93,117}($|\s) – Monero
(^|\s)4[0-9A-B]{1}[1-9A-HJ-NP-Za-km-z]{93,117}($|\s) – Monero
To protect against malware, only download software from trusted sources. If you accidentally download a rogue file, use antivirus software or VirusTotal to check for malicious intent. Malware will eventually be discovered. To check if your system is compromised, use a Notepad trick by copying and pasting a specific Bitcoin address. If the address changes, your system may be compromised, and you should scan it for malware. If your system is compromised, rebuild it to ensure no hidden backdoors remain.
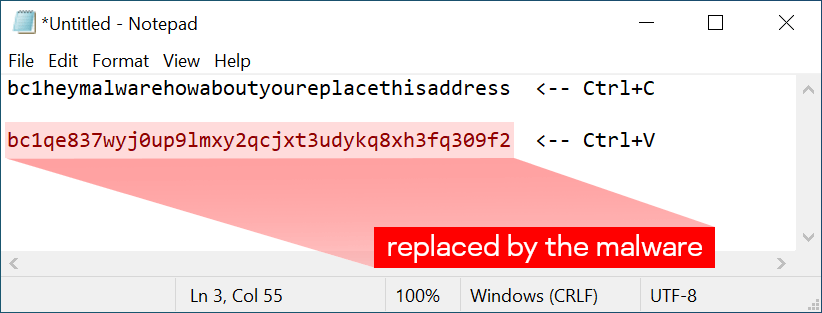
Keep yourself protected and prevent criminals from accessing your coins.