As the InterPlanetary File System (IPFS) gains popularity, it also introduces new risks. Initially developed in 2015 with Web 3.0 technology, IPFS adoption is primarily driven by concerns about data privacy and reducing reliance on centralized tech giants like Google, Microsoft, and Facebook. However, this increased adoption has attracted the attention of malicious actors who have rapidly adopted IPFS for their cybercriminal activities. This article aims to provide an overview of IPFS, explain how malicious attackers are exploiting it for phishing attacks, and offer best practices for safeguarding your organization against IPFS phishing threats.
IPFS, short for the InterPlanetary File System, is a modular set of protocols designed for organizing and transferring data. It is an open-source technology with various implementations, primarily used for decentralized data publishing, including files, directories, and websites. In simpler terms, IPFS revolutionizes how information is shared and stored on the internet, emphasizing efficiency, reliability, and decentralization.
Unlike traditional methods reliant on centralized servers, IPFS connects individual computers in a network, enabling them to collaborate and directly share information. When you access a file or website via IPFS, the system divides the data into smaller fragments and distributes them across multiple networked computers, referred to as nodes. Each fragment is assigned a unique fingerprint, known as a hash, for identification and retrieval. Rather than requesting the entire file from a single server, your computer retrieves these fragments from various sources within the network, enhancing speed and resilience to failures.
This decentralized approach reduces the risk of data loss or censorship and optimizes resource utilization, as computers share data directly among themselves, reducing the burden on centralized servers. IPFS employs cryptographic hashes to validate the authenticity and integrity of files, thwarting attackers from tampering with or deleting files. However, this decentralized nature also poses challenges for defenders trying to remove phishing sites or malicious content.
While open-source technologies encourage collaboration and innovation, they also offer opportunities for threat actors to expand their attack vectors, and IPFS is no exception, especially in the realm of phishing attacks.
IPFS phishing attacks operate similarly to phishing attacks on centralized networks. Attackers employ social engineering tactics, email and messaging platforms, and cloned websites to impersonate legitimate brands, aiming to steal users' credentials and access networks. A significant difference, however, arises from IPFS's characteristics. Once content is published on the IPFS network, it becomes accessible to anyone who can then republish it on their own node. Leveraging this distributed file system, attackers can easily create permanent and untraceable phishing sites that can remain active even after the original source is removed.
Accessing the IPFS network can be accomplished through various methods, including desktop applications, the IPFS Command Line Interface (CLI), browser extensions, web app integrations, or public gateways. In the context of IPFS phishing attacks, threat actors frequently utilize public gateways as proxies, enabling victims to open file access links, irrespective of whether they use any of the previously mentioned applications.
The following image shows an example of IPFS phishing attack. As seen in this example, the phishing page impersonating a Microsoft login page is relatively straightforward and lacks complexity - most observed IPFS phishing attacks are similarly basic.
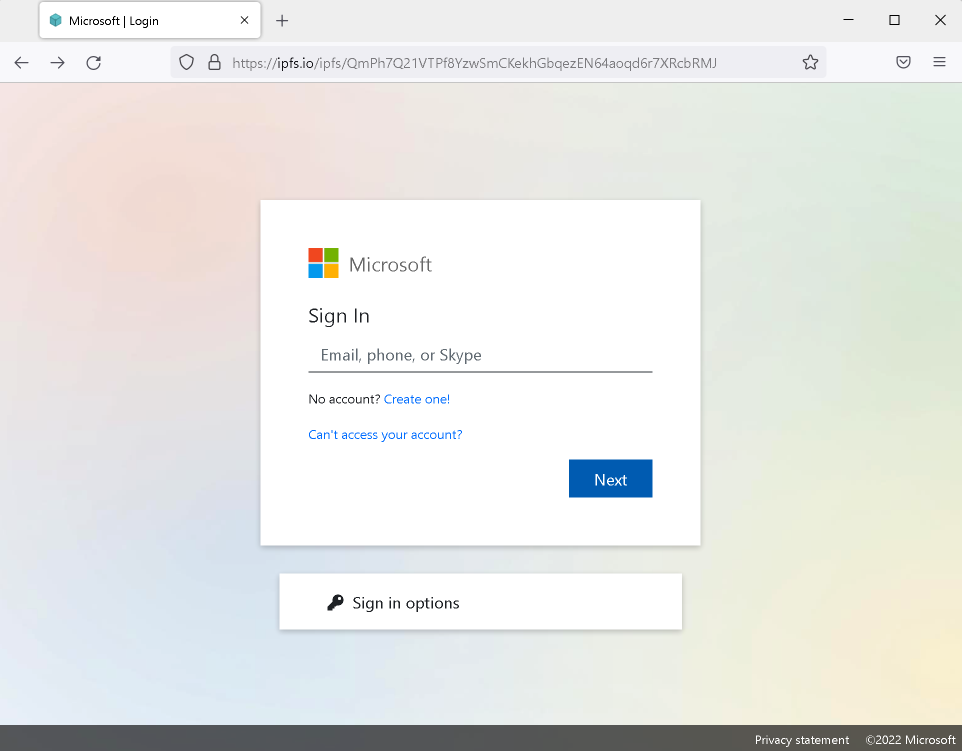
Similar to most phishing sites, distinguishing between a fraudulent site and a legitimate one can be exceedingly challenging for end-users.
While the URL clearly indicates that the content is hosted on the IPFS network, this fact alone does not signify anything inherently good or bad about IPFS content.
In conclusion, as IPFS continues to gain popularity, it also becomes a target for malicious actors seeking to exploit its decentralized nature for phishing attacks. Understanding how these attacks operate and implementing effective security measures is crucial to protect against IPFS-related threats.