A novel phishing technique called browser-in-the-browser (BitB) attack can be exploited to simulate a browser window within the browser in order to spoof a legitimate domain, thereby making it possible to stage convincing phishing attacks.
According to penetration tester and security researcher, who goes by the handle mrd0x on Twitter, the method takes advantage of third-party single sign-on (SSO) options embedded on websites such as "Sign in with Google" (or Facebook, Apple, or Microsoft).
While the default behavior when a user attempts to sign in via these methods is to be greeted by a pop-up window to complete the authentication process, the BitB attack aims to replicate this entire process using a mix of HTML and CSS code to create an entirely fabricated browser window. (The Hacker News)
DEMO

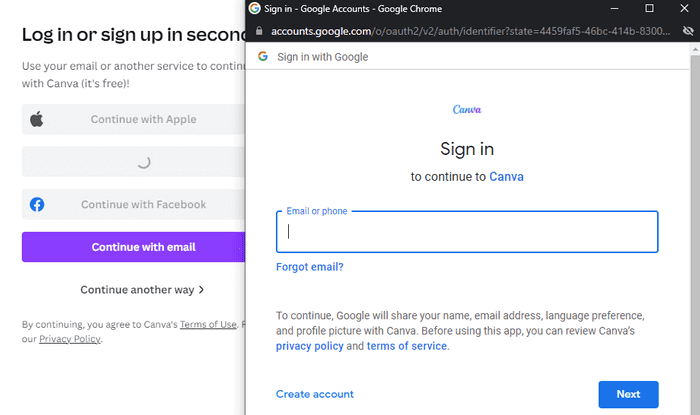
Quite often when we authenticate to a website via Google, Microsoft, Apple etc. we’re provided a pop-up window that asks us to authenticate. The image below shows the window that appears when someone attempts to login to Canva using their Google account.
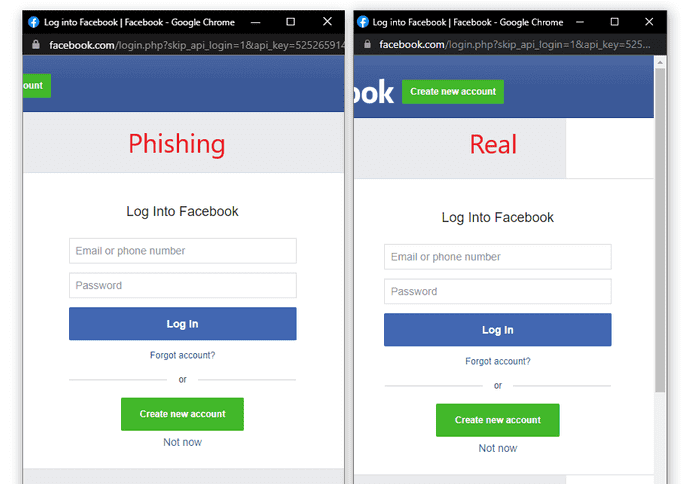
Fortunately for us, replicating the entire window design using basic HTML/CSS is quite simple. Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and its basically indistinguishable. The image below shows the fake window compared with the real window. Very few people would notice the slight differences between the two.
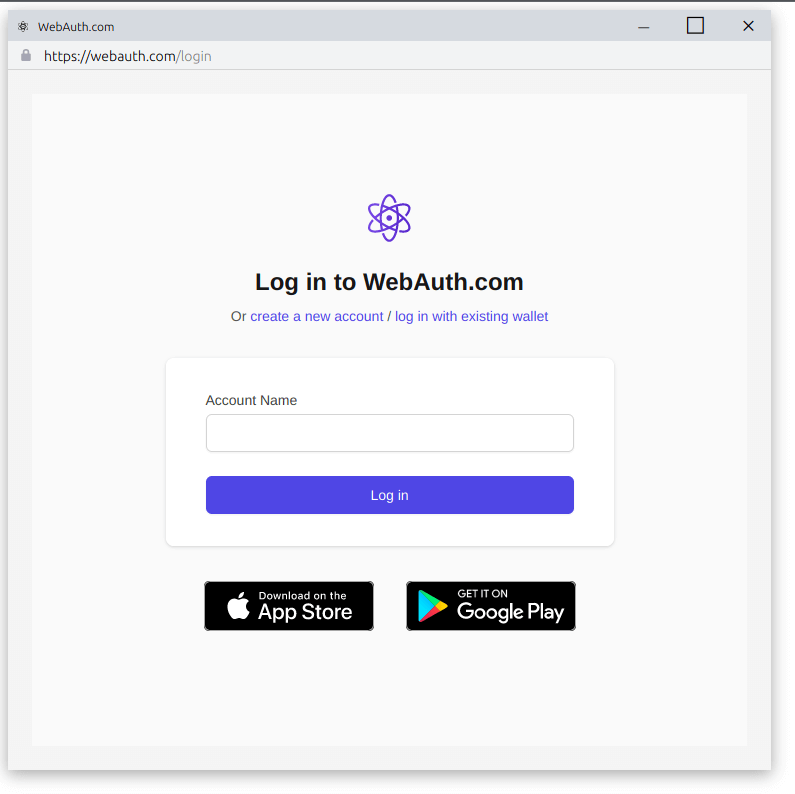
We've made an example of phishing website for webauth.com, just for the sake of learning. What you see is fake pop-up window, made in HTML/CSS, so from that point an attacker can make URL to look legit and deceive victim into logging in.
Real login windows are browser windows, and they act that way. You can maximize and minimize them and move them anywhere on the screen. Fake pop-ups are bound to the page where they’re located. They can also move freely and cover buttons and images, but only inside their boundaries — that is, within the browser window. They cannot go outside it. That difference should help you spot them.