Coinmarketcap shared a story, about crypto investor who lost $1.7M in hot wallet hack.
The article stated:
The founder of a DeFi venture fund has lost more than $1.7 million after his hot wallet was targeted in an audacious attack — and has warned that even sophisticated users are at risk of exploits.
DeFiance Capital founder Arthur Cheong — known as Arthur_0x on Twitter — confirmed that many of his NFTs were stolen as a result of the hack, and they're now being advertised for sale on OpenSea.
The victim itself said:
"Was pretty careful and stuck with only using hardware wallet on PC until I start trading NFT more regularly. Hot wallet on mobile phone is indeed not safe enough."
The entire story is available on their website.
One of our followers asked us to explain the details about attack vector and how attackers gained unauthorized access. Despite the fact that there was not so many details shared about attack, we tried to gather as much as we can. Firstly Arthur_0x (victim) shared screenshot of email that he received, which was an entry point of attackers.
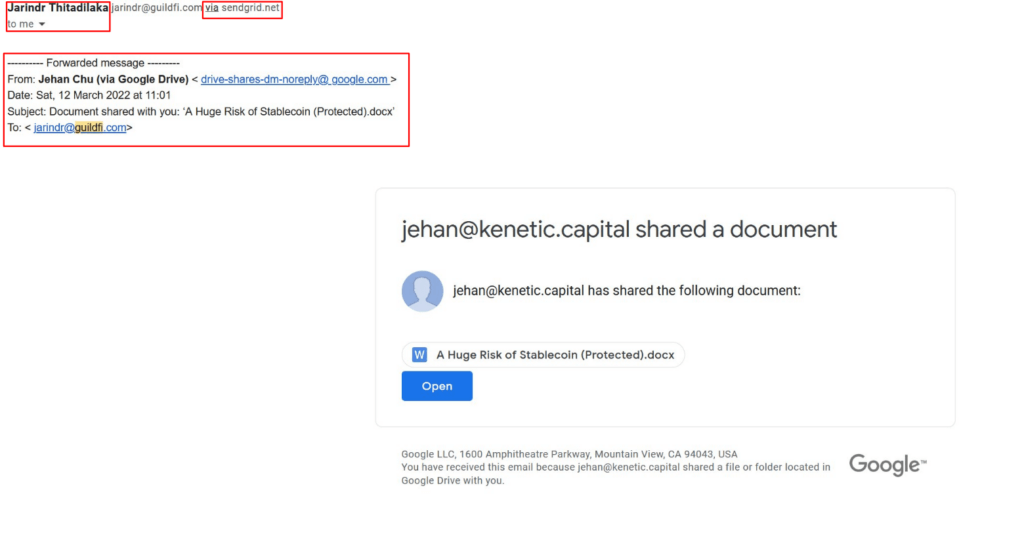
Suspected group behind this attack is known to perform high-quality social engineering attacks, such as this one. In this scenario, it appeared as a notification of a shared document via Google Drive, as it is shown in picture above.
We are aware that many users can be confused by such emails and don't understand the technical details of it. Let's begin by analyzing this email which victim received. First let's brake all names by individual parts:
So what really happened here?
From the picture above the chain of that email went in the following sequence:
Jehan -> Jarindr -> forwards -> Arthur
But it is obvious that forward message was altered, as you can see an empty space before google.com (drive-shares-dm-noreply@ google.com), and that was probably used to avoid triggering Google spam filters. Another important question is; why attackers used all those names?
Very likely for the purpose of raising the level of trust by using previously known people, that may be somehow connected with each other. Imagine if you received an email with some important data from someone you know. By that attacker will most definitely attract more attention and gain higher level of trust, unlike if you receive from someone that has no connection with you.
As securelist.com stated:
According to our research this year, we have seen BlueNoroff operators stalking and studying successful cryptocurrency startups. The goal of the infiltration team is to build a map of interactions between individuals and understand possible topics of interest. This lets them mount high-quality social engineering attacks that look like totally normal interactions. A document sent from one colleague to another on a topic, which is currently being discussed, is unlikely to trigger any suspicion. BlueNoroff compromises companies through precise identification of the necessary people and the topics they are discussing at a given time.
There is also one more detail if you look closely (via sendgrid.com).
According to their website (sendgrid.com) it seems to be a legitimate and reputable business, which is probably why Gmail accepts MIME header customization (or sender address forgery in the case of an attack) with nothing more than the short remark "via sendgrid.net".
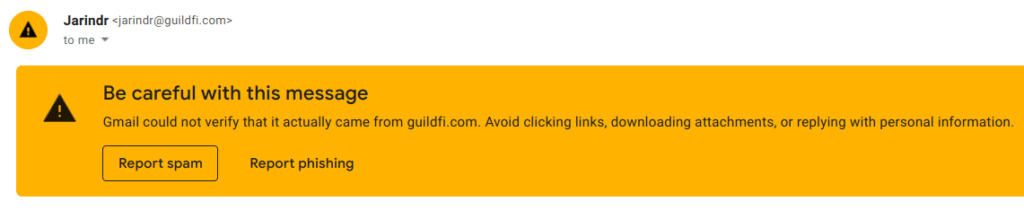
If we use non-reputable source and try to send unauthenticated message, Gmail will warn us:
Second phase of attack is concentrated on infecting a victim, by using this file: A Huge Risk of Stablecoin (Protected).docx. We have executed file in isolated environment, where we gather information to better understand how infection happened.
Malicious docx document is trying to exploit CVE-2017-0199, but before we continue you need to understand what CVE-2017-0199 vulnerability is.
Description of CVE-2017-0199:
A remote code execution vulnerability exists in the way that Microsoft Office and WordPad parse specially crafted files. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Exploitation of this vulnerability requires that a user open or preview a specially crafted file with an affected version of Microsoft Office or WordPad. In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted file to the user and then convincing the user to open the file. The update addresses the vulnerability by correcting the way that Microsoft Office and WordPad parses specially crafted files, and by enabling API functionality in Windows that Microsoft Office and WordPad will leverage to resolve the identified issue.
Here you can see practical explanation of CVE-2017-0199 by security researcher Didier Stevens:
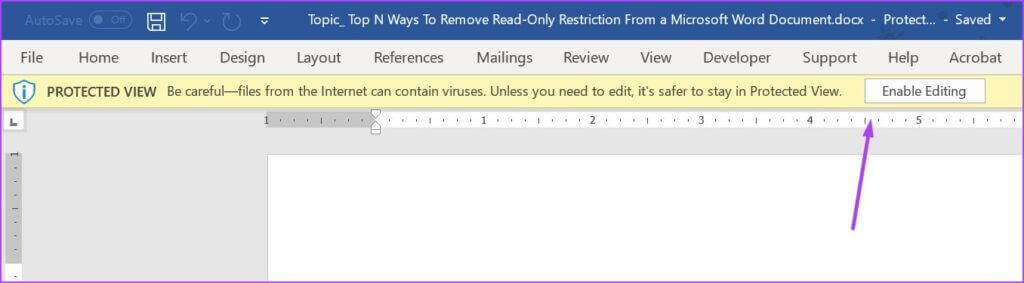
When a file is downloaded to a device running Windows, a Mark of the Web (MOTW) attribute is added to the file, identifying its source as being from the internet. Currently, when a user opens a file with the Mark of the Web (MOTW) attribute, a SECURITY WARNING banner appears, with an Enable content button. If the user selects Enable content, the file is considered a Trusted Document and macros are allowed to run. The macros will continue to run even after the change of default behavior to block macros in files from the internet is implemented, because the file is still considered a Trusted Document.
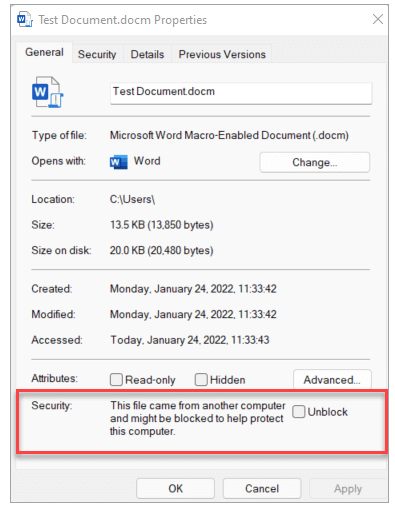
In that case document will give you security warning to enable content, which most of the time should be an indicator of possibly infected file.
The exploit relies on fetching remote content via an embedded URL inside one of the document meta files. Here you can see an example of malicious URL (secure.azureword.com), which was used to remotely download and proceed infection.
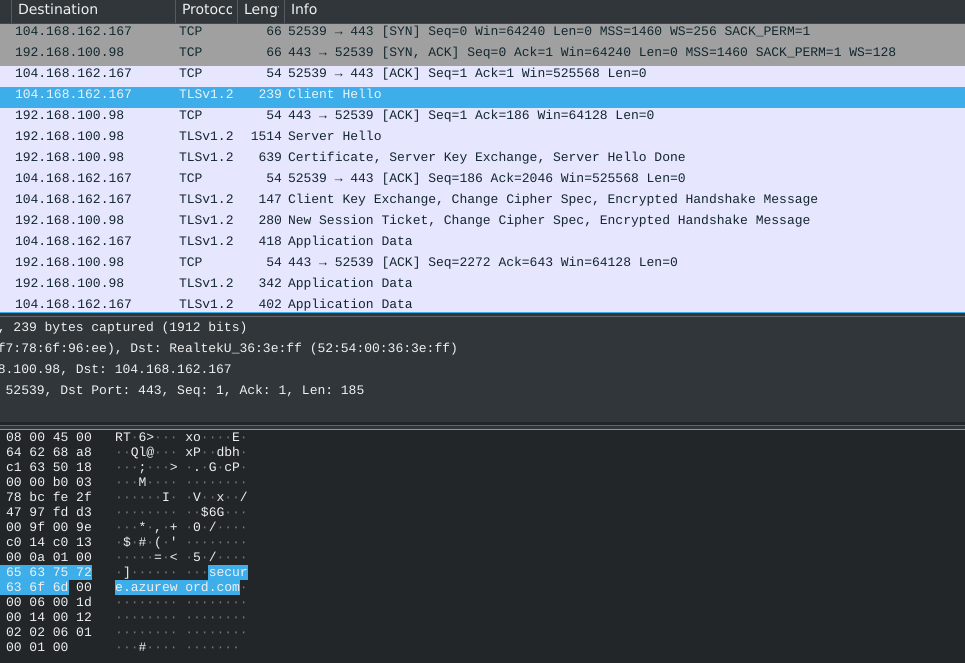
We used Whireshark to capture all HTTP traffic, as you can see from the picture Whireshark captured connection to secure.azureword.com (malicious domain):
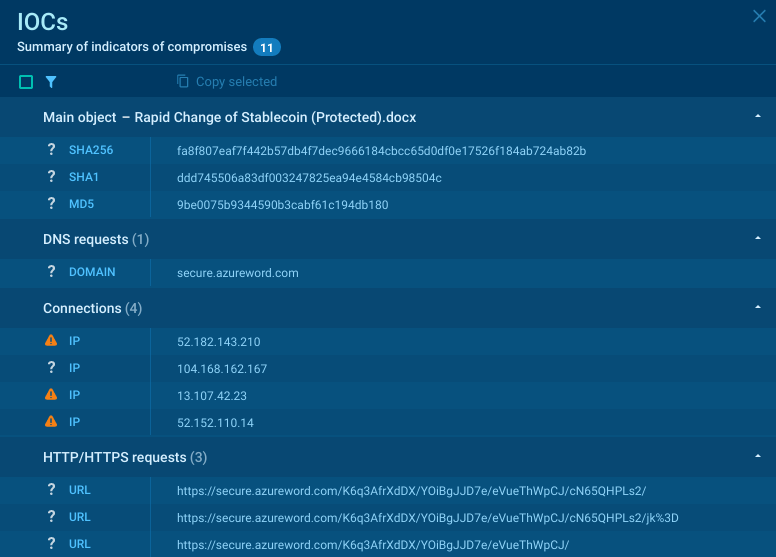
IoC:
Once malware gains access to a system, it often looks to be there for a long time. This behavior is known as persistence.
Securelist.com has already visualize an infection chain:
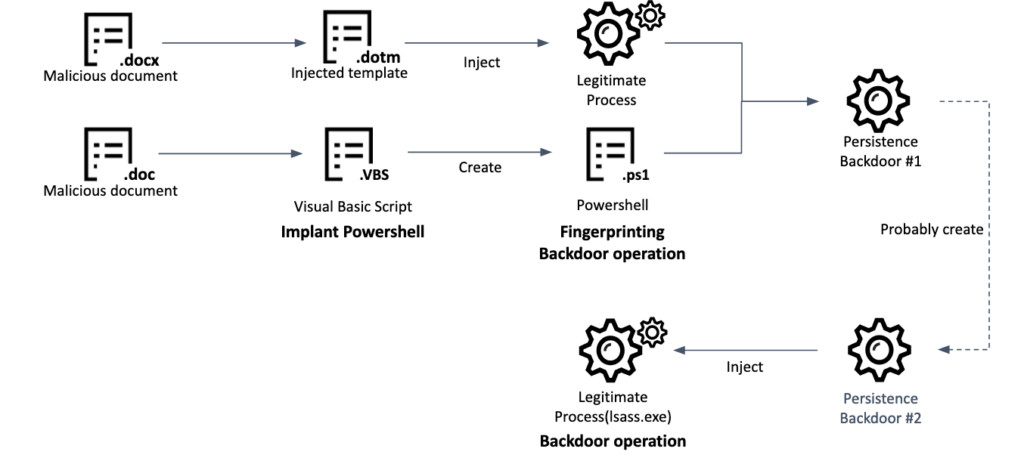
After successful infection, attackers will monitor and track for any valuable data on victim's PC, and from there, we can only imagine how valuable was for them crypto assets that victim owned.
Since this backdoor is not active anymore, we couldn't execute fully, so this is only a summary of what happened in case of Arthur_0x. By saying that backdoor is not active anymore it doesn't necessary mean that there will be no newer version and possibly more advanced than this one.