The rise in popularity of cryptocurrencies has encouraged cybercriminals to find innovative ways to attack markets, users and any structure where cryptocurrencies are stored. In simple words, if an attacker is able to exploit some area of a chain, smart contract, exchange or illegitimately withdraw cryptocurrency, it would be deemed as a hack or stealing. Scammers around the world took home a record of $14 billion in cryptocurrency in 2021.
Couple weeks ago we published an article: Investigation of websites and Telegram groups that are stealing private keys, so in case you missed it, read and learn how to recognize and avoid phishing websites.
Let's begin...
Everything started with another scam group that promoted non-existing giveaway from Proton. Link led us to a phishing website, that tries to steal private keys from Proton users.

Never click on suspicious or malicious links, when you click on unverified links or download suspicious apps you increase the risk of exposure to malware.
When we tried to send a request (using dummy key), it called PHP file (access.php) and store somewhere on a server.
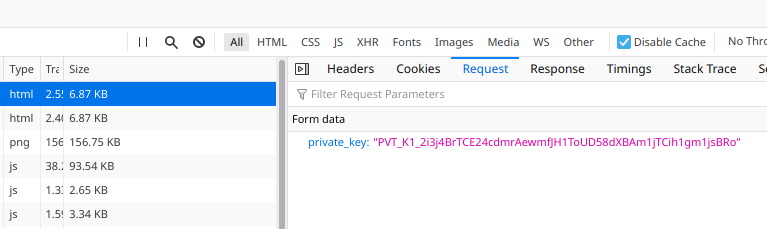
Luckily this scammer misconfigured server, which gave us ability to list through files (directory listing).
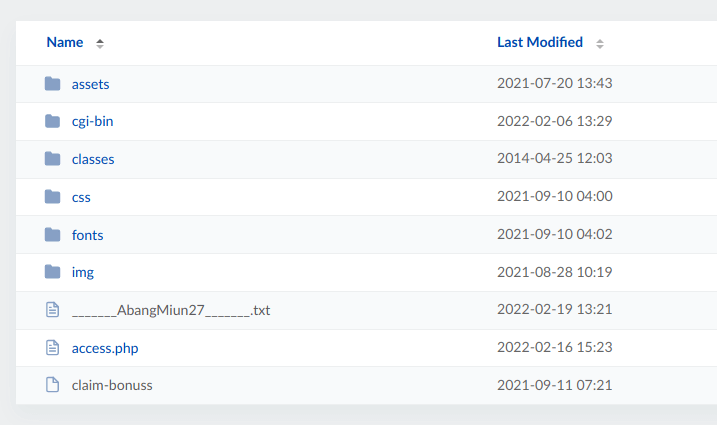
File named "_AbangMiun27_.txt" contained all the sensitive information, including private keys, IP addresses and time entries.
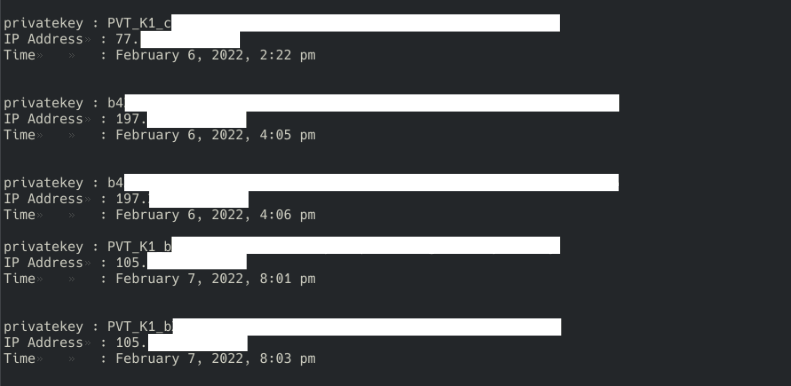
We checked those private keys and try to retrieve with which account they are associated. By converting from PVT_K1 to EOS older format gave us ability to find PUB_K1, but luckily all accounts were not holding any funds and there was no transfers.
We strongly advise all users that entered their private keys to change it. Soon we will publish article on how to change OWNER and ACTIVE keys.
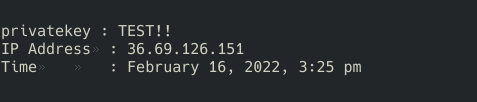
Scammer IP address:
whois 36.69.126.151
inetnum: 36.69.112.0 - 36.69.127.255
descr: PT TELKOM INDONESIA
descr: STO Gambir 3rd Floor
descr: Jl. Medan Merdeka Selatan No. 12
descr: Jakarta 10110
country: ID
admin-c: AR165-AP
tech-c: HM444-AP
abuse-c: AI598-AP
status: ASSIGNED NON-PORTABLE
mnt-by: MAINT-TELKOMNET
mnt-irt: IRT-IDTELKOM-ID
last-modified: 2021-01-26T22:06:47Z
source: APNIC
With this scam there was two associated email accounts:
Admin Email: cimolly07@gmail.com
Registry Tech ID: Not Available From Registry
Tech Name: Ollie N/A
Tech Organization:
Tech Street: jl,sudirman jl,sudirman
Tech City: jakarta
Tech State/Province: DKI JAKARTA
Tech Postal Code: 56784
Tech Country: ID
Tech Phone: +62.82283737512
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: cimolly07@gmail.com
Name Server: ns1.domosquare.com
Name Server: ns2.domosquare.com
Remember, there are more sophisticated attacks, scams out there, so act responsibly and carefully.
Learn how to back up your WebAuth private key, and remember never share your private key to anyone else.